Azure Landing Zone for Beginners: From Empty Subscription to Ready-for-Prod in a Weekend
Introduction: Your Weekend Cloud Transformation
The cloud offers unparalleled flexibility and scale, but diving into a fresh Azure subscription without a plan can quickly lead to complexity, security gaps, and unmanageable costs. That’s where the Azure Landing Zone concept comes in. It’s Microsoft’s guidance for setting up a well-architected, secure, and scalable environment that’s ready to host your applications and data.
This guide is for beginners – those who have an empty Azure subscription and a weekend to spare. We’ll walk you through the essential steps to lay down a robust foundation, making your Azure environment “ready for production” in just a few focused hours. No prior enterprise architecture degree required!

What is an Azure Landing Zone and Why Do You Need It?
An Azure Landing Zone is essentially a predefined, secure, and governed environment designed to host your workloads. It’s built on Microsoft’s Cloud Adoption Framework (CAF) and addresses critical concerns like:
- Security: Implementing baselines for network segmentation, access control, and threat protection.
- Governance: Setting up policies, cost management, and resource organization.
- Scalability: Designing a network and subscription structure that can grow with your needs.
- Identity: Integrating with your existing identity systems or establishing new ones.
- Operations: Laying the groundwork for monitoring and management.
Think of it as building a house. You wouldn’t just drop furniture on bare land. You’d pour a foundation, erect walls, install plumbing and electricity. An Azure Landing Zone is that robust foundation for your cloud house.
The Weekend Plan: Your Step-by-Step Guide
Here’s our action plan for your weekend Azure transformation. We’ll focus on the core components you can realistically set up.
Day 1: Foundation & Identity
Step 1: Azure Subscription Design & Management Groups
An empty subscription is your starting point. For a beginner, we’ll focus on a single subscription initially, but understand the concept of Management Groups for future scalability.
- Your Root Management Group: All your subscriptions fall under a “Tenant Root Group” by default. This is where you’ll apply high-level policies.
- Create Management Groups (Optional but Recommended): Even with one subscription, creating a simple hierarchy (e.g.,
Platform,Landing Zones) prepares you for growth. For this weekend, we’ll keep it simple: one subscription, but know that Management Groups are your enterprise-scale solution.
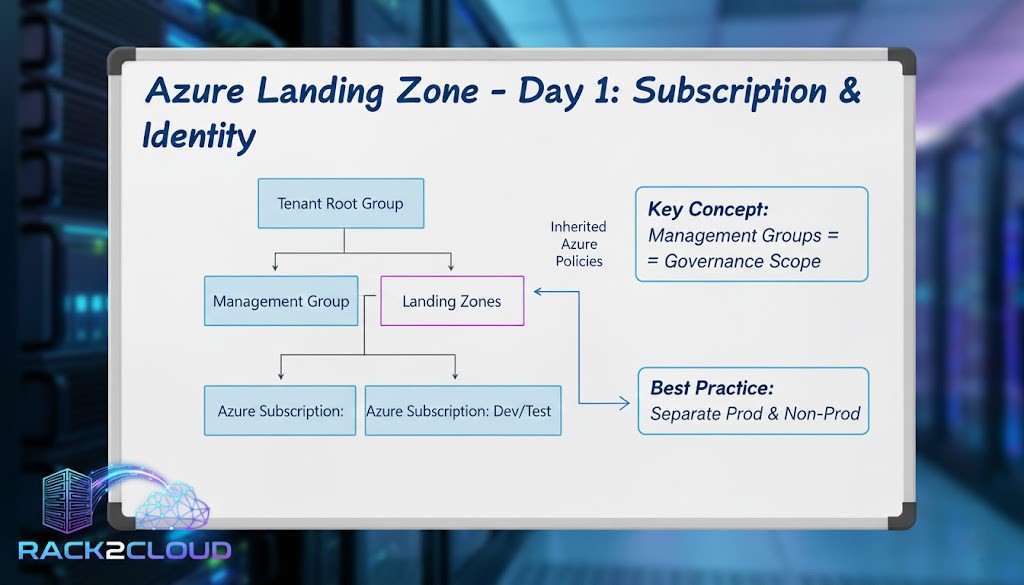
Action: Navigate to Management Groups in the Azure portal and create a Platform Management Group under your Tenant Root. Move your current subscription under this Platform MG.
Step 2: Identity and Access Management (IAM)
Identity is the cornerstone of security. Azure Active Directory (now Microsoft Entra ID) is your identity provider.
- Understand Entra ID: Your Azure subscription is already linked to an Entra ID tenant. This is where your users, groups, and applications will reside.
- Create Administrative Users/Groups: Avoid using the global administrator account for daily tasks.
- Create a dedicated security group for Azure Administrators (e.g.,
Azure-Admins). - Create a personal user account for yourself (if you’re currently using a global admin or root account) and add it to
Azure-Admins. - Assign the
Ownerrole at the subscription scope to yourAzure-Adminsgroup. This grants necessary permissions.
- Create a dedicated security group for Azure Administrators (e.g.,
- Enable Multi-Factor Authentication (MFA): This is non-negotiable for all administrative accounts.
- Action: Go to Microsoft Entra ID > Properties > Manage Security Defaults and enable security defaults for MFA, or set up Conditional Access policies if you have Entra ID P1/P2.

Day 2: Networking, Governance & Security Baselines
Step 3: Network Topology (Hub-Spoke Model)
A robust network is crucial. The Hub-Spoke model provides centralized control and simplified connectivity.
- The Hub VNet: This is your central network, hosting shared services like firewalls, VPN gateways, and DNS.
- Create a new Resource Group:
rg-network-hub-prod-eastus(or your preferred region). - Create a Virtual Network (VNet) in this RG:
vnet-hub-prod-eastus. Choose an appropriate address space (e.g., 10.100.0.0/16). - Create at least two subnets:
GatewaySubnet(for VPN/ExpressRoute) andAzureFirewallSubnet(for your firewall).
- Create a new Resource Group:
- A Spoke VNet (Your First Workload VNet): This is where your applications will live.
- Create a new Resource Group:
rg-app01-prod-eastus. - Create a VNet:
vnet-app01-prod-eastus(e.g., 10.10.0.0/16). - Create a subnet for your application:
snet-web-prod-eastus.
- Create a new Resource Group:
- VNet Peering: Connect your Spoke VNet to your Hub VNet. This allows resources in the spoke to communicate with shared services in the hub.
- Action: Go to your
vnet-hub-prod-eastusand add peering tovnet-app01-prod-eastus(and vice-versa).
- Action: Go to your
Additional Resources:
- Microsoft Azure Landing Zone – CAF
- Exam Ref AZ-900 Microsoft Azure Fundamentals
- Azure Landing Zone:Practical Guide to Cloud Foundations
This architectural deep-dive contains affiliate links to hardware and software tools validated in our lab. If you make a purchase through these links, we may earn a commission at no additional cost to you. This support allows us to maintain our independent testing environment and continue producing ad-free strategic research. See our Full Policy.