Deterministic IaC Pipelines: Turning Terraform Plans into Signed Contracts Between Security and Operations
I’ve spent the better part of two decades watching Infrastructure as Code (IaC) evolve. I remember the days of “shaky Bash scripts” held together by hope and cron jobs, and I’ve watched us graduate to “sophisticated Terraform modules.” But here is the hard truth that usually only hits you during a post-mortem: A Terraform apply is not a guarantee of state; it is merely a request.
I still have nightmares about a 2 a.m. incident back in 2019. A “minor” security group change—approved by a junior dev and rubber-stamped by a sleepy lead—passed through a loose CI/CD pipeline. The pipeline turned green. It said “Success.” But in reality, that change inadvertently exposed a production RDS instance to the entire public internet. We were compromised for six hours before anyone noticed.
That night, I realized something critical: Unless your pipeline acts as a legally binding, cryptographically signed contract between your Security and Operations teams, you aren’t doing IaC. You’re just gambling with automation at scale. True determinism isn’t just about getting the same output twice; it’s about ensuring that what you approve is exactly what gets deployed, with zero variance, zero drift, and zero surprises.
The Anatomy of a Deterministic Pipeline
In a standard “leaky” pipeline, an engineer commits code, a runner executes plan, and then apply. The gap between those steps is where the devil resides. A deterministic pipeline treats the binary plan file as an immutable artifact. It doesn’t just run code; it interrogates it.
Decision Framework: Selecting Your Validation Logic
I often get asked, “Why not just use the native tools?” Here is how I break down the decision when I’m architecting a new platform:
| Feature | Open Policy Agent (Rego) | HashiCorp Sentinel | Cloud-Native (AWS Config/Azure Policy) |
| Ecosystem | Universal (K8s, IaC, HTTP) | Terraform/Vault Exclusive | Cloud Specific |
| Enforcement | Pre-computation (Shift Left) | Runtime (During Plan) | Post-deployment (Reactive) |
| Licensing | Open Source (Apache 2.0) | Paid (Terraform Enterprise) | Usage-based |
| Best For | Multi-cloud complexity | Pure HashiCorp shops | Compliance-heavy public cloud |
My Take: If you are building for the next decade, choose OPA. It is the only way to maintain a single source of truth for policies across your Nutanix clusters, your Kubernetes namespaces, and your public cloud footprint simultaneously.
Day 2 Operations: Preventing “State Rot” & Sovereign Drift
The most common failure I see in mature organizations is “State Rot.” This happens when the terraform.tfstate deviates from the actual hardware or cloud API reality. But in 2026, we have two new, far more dangerous problems: Sovereign Drift and Licensing Liability.
If your automation works perfectly but deploys a workload to a non-sovereign region, you’ve broken the law. If it scales your cluster beyond your paid entitlements, you’ve broken the budget.
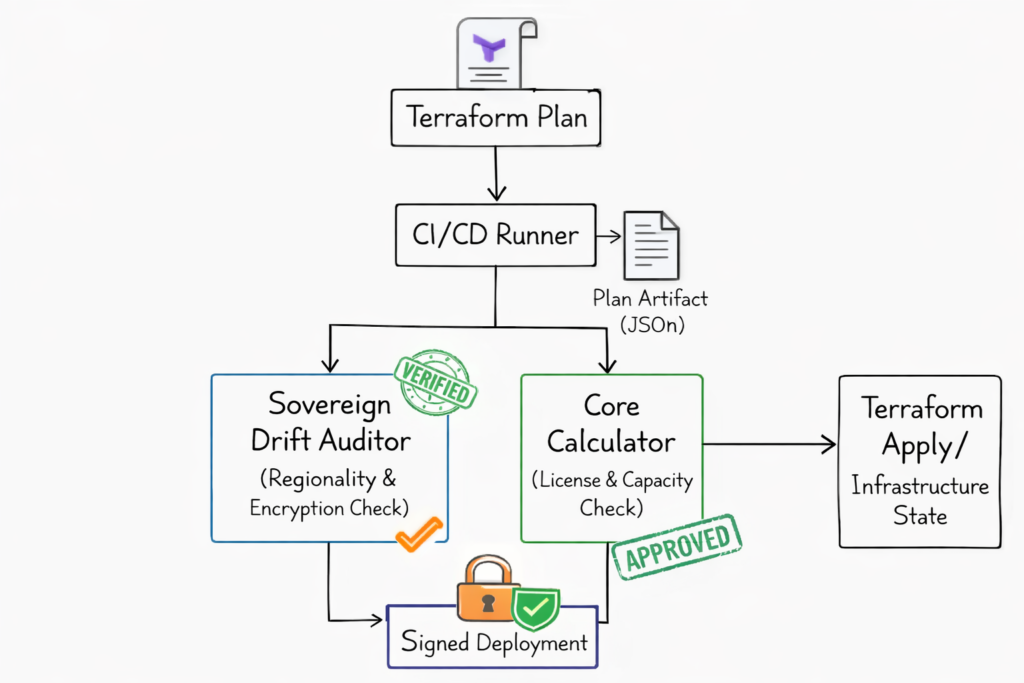
To combat this, your pipeline must enforce Strict Plan Integrity using the right tools for the job:
- Sovereign Compliance (The “Lawyer” Check):I strictly enforce a “Sovereignty Gate” using the Sovereign Drift Auditor v1. This tool ingests your plan.json and instantly flags any provider regions that violate data residency requirements or storage volumes lacking AES-256 encryption. It’s an automated auditor that works faster than any human ever could.
- Financial Guardrails (The “CFO” Check):Before you hit apply, you need to know if you can afford the deploy. I configure pipelines to cross-check the plan against the VMware Core Calculator. If your Terraform code tries to spin up a node count that exceeds the 320 billable cores defined in your VMware Renewal Estimator strategy, the pipeline fails. No “True-Up” surprises allowed.
- Network Logic (The “Security” Check): If you are re-platforming from VMware to Nutanix, you cannot afford to manually rebuild your micro-segmentation policies. Use the NSX-T Translator to deterministically map your existing NSX-T distributed firewall rules directly into Nutanix Flow categories. This ensures the security posture you signed off on in VMware is exactly the one you inherit in Nutanix—zero drift, zero “lost” rules.
The FinOps Angle: CapEx vs. OpEx
Building a deterministic pipeline has a higher initial CapEx (engineering hours to write Rego policies and configure the Sovereign Drift Auditor). However, the OpEx savings are astronomical. I’ve seen teams reduce “remediation toil” by 60% after implementing automated plan signing. You stop paying for senior architects to troubleshoot “why this VPC is different from the other one” and start paying them to build new features.
Counterpoint: Does Determinism Kill Agility?
I hear this constantly from developers: “Strict pipelines slow down my hotfixes.”
My response is simple: A hotfix that isn’t deterministic is just a “hot-break” waiting to happen. If your pipeline is too slow to handle an emergency, the problem isn’t the determinism; it’s your architecture.
If you’re still running a monolithic state file for your entire production environment, stop. Break your state files into smaller, decoupled units. Refer to our Hypervisor Alternatives Guide to see how modular architecture scales better across different stacks. Speed comes from modularity, not from cutting corners on safety.
Conclusion: The Architect’s Mandate
Infrastructure is no longer about racking servers; it is about managing the integrity of state. If your security team has to “audit” your infrastructure after it’s built, you’ve already lost. The audit should happen inside the pipeline, triggered by the code commit, validated by the Sovereign Drift Auditor, and sealed with a digital signature.
Think Like an Architect: Design the system so that it is impossible to deploy an unverified change.
Build Like an Engineer: Use OPA, OIDC, and immutable plan artifacts to enforce that design.
Additional Resources:
- HashiCorp: Terraform Security Best Practices
- Open Policy Agent: Introduction to Rego
- NIST 800-204: Security Strategies for Microservices
Editorial Integrity & Security Protocol
This technical deep-dive adheres to the Rack2Cloud Deterministic Integrity Standard. All benchmarks and security audits are derived from zero-trust validation protocols within our isolated lab environments. No vendor influence.
Get the Playbooks Vendors Won’t Publish
Field-tested blueprints for migration, HCI, sovereign infrastructure, and AI architecture. Real failure-mode analysis. No marketing filler. Delivered weekly.
Select your infrastructure paths. Receive field-tested blueprints direct to your inbox.
- > Virtualization & Migration Physics
- > Cloud Strategy & Egress Math
- > Data Protection & RTO Reality
- > AI Infrastructure & GPU Fabric
Zero spam. Includes The Dispatch weekly drop.
Need Architectural Guidance?
Unbiased infrastructure audit for your migration, cloud strategy, or HCI transition.
>_ Request Triage Session





