$7,200 Zombie Load Balancers: The Taxonomy of Failure & Why ClickOps Breaks Planetary Scale

The “$7,200” ClickOps Tax: A single untagged Load Balancer, forgotten for 36 months, wasted thousands. Multiply that by 400 POCs, and you have a financial problem that no amount of cost optimization tooling can fix.
If you walk into a warehouse and throw a box in the middle of the aisle without a barcode, that box effectively ceases to exist to the logistics system. It takes up space, it creates a tripping hazard, but it cannot be shipped, tracked, or audited.
The Cloud is no different. The moment a resource lacks identity, it falls outside every automation, security boundary, and financial control you rely on.
Key Takeaways
- $7,200/ALB × 36 months: The cost of one “ClickOps” mistake nobody catches.
- Untagged = Dark Matter: Security tools (Wiz/Prisma) and Cost tools (Vantage) rely on scopes. If a resource lacks a tag, it is invisible to your control plane.
- 5 Mandatory Tags:
CostCenter,Environment,Geo,Owner,Sensitivity. Zero more, zero less. - Policy DENIES Creation: Do not rely on memos. Use Azure Policy or AWS SCPs to block deployment of untagged resources.
- Audit “Unallocated” Spend: If your “Unknown” bucket is >5% of the bill, you don’t have a cloud strategy; you have a digital landfill.

The Physics of “Dark Matter” Infrastructure
Every modern control plane—Security, Cost, and Operations—depends on Metadata Scopes. You don’t tell the backup software to “Back up Server A.” You tell it to “Back up everything tagged Sensitivity:Confidential.”
If a resource lacks a tag, it falls outside the scope. It becomes Operational Dark Matter.
In large environments, we routinely see 5–15% of resources fall into this category within a year.
- Unsecured: Vulnerability scanners skip it because it doesn’t match the
Env:Prodscope. - Unbillable: FinOps tools cannot allocate the cost because it lacks a
CostCenter. - Unowned: When it breaks at 3 AM, PagerDuty doesn’t know which
Ownerto wake up.
// THE CONTROL PLANE EQUATION
Control_Plane = Resource + Identity + Context
Click_Ops = Resource + NULL_Identity + NULL_Context
>> RESULT: Control_Plane = NULLThe Horror Story: The $7,200 Zombie Load Balancer
We recently audited a client environment to find the source of “Unallocated Spend.” We found a single AWS Application Load Balancer (ALB) that had been running for 36 months.
The Timeline of Waste
- Year 1 (The Click): A developer spins up an ALB via the Console (ClickOps) for a quick “Friday Afternoon POC.” They skip the tags because “it’s just a test.”
- Year 2 (The Departure): The developer leaves the company. The resource has no
Ownertag, so offboarding scripts miss it. - Year 3 (The Invisibility): The ALB sits idle. It processes zero traffic, but bills for hourly availability.
The Math
$200/month (ALB Base + Idle LCU) × 36 Months = $7,200.
Why didn’t anyone catch it?
Because it didn’t belong to a budget code. It wasn’t in Terraform state. It wasn’t in the security scope. It was invisible until we audited the raw bill.
Multiply this by every POC, intern project, and late-night hotfix in your history, and you don’t have “cloud sprawl” — you have a digital landfill.
The Solution: The “Golden Schema”
Stop debating which of the 50 possible tags you need. You only need five. These five tags answer the fundamental questions of existence for any compute resource.
| Tag Key | Example Value | Operational Function |
CostCenter | CC-102, Eng-Core | Financial Routing. Determines who pays the bill. If this is missing, finance cannot allocate spend. |
Environment | Prod, Dev, Stage | Security Scope. Determines firewall strictness, IAM access levels, and blast radius. |
Geo | EU-West, US-East | Data Residency. Determines compliance boundaries (GDPR) and latency expectations. |
Owner | team-ops@domain.com | Escalation Routing. Who do we page when this breaks? |
Sensitivity | Public, Confidential | Compliance Scope. Determines Backup frequency, Encryption requirements, and DLP auditing. |
The Rule: If a resource does not have these five tags, it does not get deployed.
The Enforcement Layer: Governance as Code
The only reliable way to eliminate ClickOps sprawl is to make untagged deployments technically impossible. You must enforce this with code.
Option A: Azure Policy (Deny Effect)
This example enforces the schema at the control plane, not the UI, which is why it works even against privileged users. If a user tries to create a Resource Group or Resource without the CostCenter tag, the API rejects the request.
JSON
{
"mode": "Indexed",
"policyRule": {
"if": {
"allOf": [
{
"field": "tags['CostCenter']",
"exists": "false"
}
]
},
"then": {
"effect": "deny"
}
}
}
Option B: AWS Service Control Policy (SCP)
This must be applied at the AWS Organization Root to be effective against account-level administrators. It blocks RunInstances or CreateVolume if tags are missing.
JSON
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "DenyUntaggedResources",
"Effect": "Deny",
"Action": "ec2:RunInstances",
"Resource": "arn:aws:ec2:*:*:instance/*",
"Condition": {
"Null": {
"aws:RequestTag/CostCenter": "true"
}
}
}
]
}
The Developer Experience:
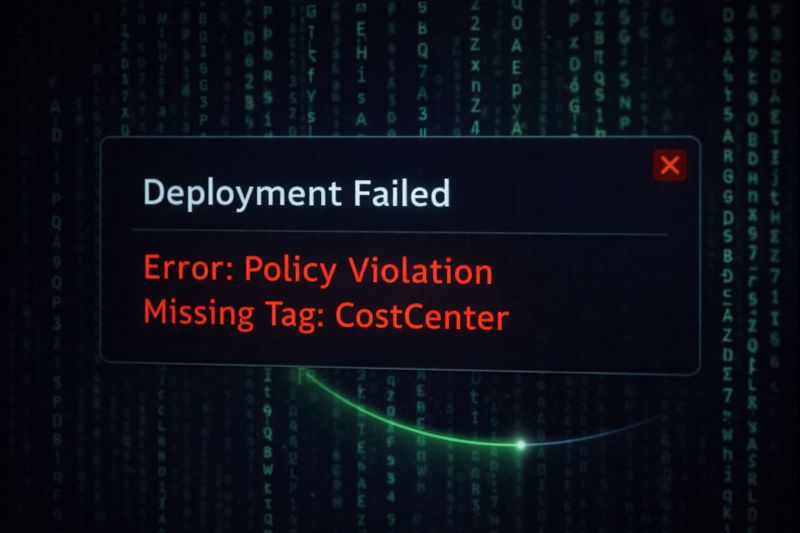
When a developer tries to “ClickOps” a VM and skips the tags, they hit a rigorous error: Deployment Failed. Policy Violation. This forces them to abandon the manual portal and use Infrastructure as Code (Terraform/Bicep), where tags are applied automatically via modules.
The Hierarchy: Where Policies Live
Where do you apply these policies? Not at the Subscription level (too much manual work). You apply them at the Management Group Root.
The Deployment Matrix: Pick Your Weapon
Not every organization can start with “Deny everywhere.” The right approach depends on organizational maturity and blast radius tolerance.
| Approach | Scope | Effect | Friction | Shadow IT Kill Rate |
| The Iron Fist | Root MG | Deny | High | 100% |
| Training Wheels | Root MG | Audit → Deny | Medium | 90% |
| Geo Sandbox | EU/US MGs | Deny | Low | 70% |
Recommendation: Start with Training Wheels. Set the policy to Audit for 2 weeks to see what breaks, then flip the switch to Deny.
Verdict: No Identity, No Compute
There is an old saying in operations: “No Ticket, No Laundry.” It means if you don’t follow the process, you don’t get the service.
Cloud Governance is the same. “No Identity, No Compute.”
It seems harsh to block deployments over metadata, but the alternative is a chaotic sprawl of “Dark Matter” infrastructure that bleeds budget and hides security risks.
- Audit your “Unallocated” or “Unknown” cost bucket today.
- If it represents more than 5% of your bill, you don’t have a cloud strategy; you have a digital landfill.
Additional Resources
Add these at the bottom under a ## References & Further Reading header.
- Microsoft Learn: Azure Policy definition structure – Azure Policy
- AWS Documentation: Service control policies (SCPs) – AWS Organizations
- FinOps Foundation: Allocation of Shared Costs (Validates the “CostCenter” requirement).
This architectural deep-dive contains affiliate links to hardware and software tools validated in our lab. If you make a purchase through these links, we may earn a commission at no additional cost to you. This support allows us to maintain our independent testing environment and continue producing ad-free strategic research. See our Full Policy.