Terraform Error: “Tagging Not Allowed” (The Fix)
This technical deep-dive has passed the Rack2Cloud 3-Stage Vetting Process: Lab-Validated, Peer-Challenged, and Document-Anchored. No vendor marketing influence. See our Editorial Guidelines.
There is nothing quite like the adrenaline spike of a failed terraform apply five minutes before your weekend begins. You’ve implemented a robust “Global Tagging Strategy” (perhaps using default_tags in your provider block), and suddenly, your pipeline slams into a wall.
The error usually screams about a 403 Forbidden (Policy Deny) or a 400 BadRequest claiming that a specific resource “does not support tags.” Here is why your perfect governance strategy just broke your build—and how to fix it without rolling back.
Key Takeaways
- The Conflict: Azure Policy “Deny” effects often trigger before Terraform can apply tags if they aren’t inline.
- The Limitation: Some legacy or sub-resources (like certain peering links or diagnostic settings) do not support tags, yet provider-level tags try to force them.
- The Fix: Use lifecycle blocks to explicitly ignore tag drift on unsupported resource types.

The Error: 403 Forbidden / Tagging Not Supported
You will see one of these two variations in your stderr:
Scenario A: The Policy Block (Resource Group)
Plaintext
Error: creating Resource Group "rg-production-001": resourcegroups.ResourceGroupsClient#CreateOrUpdate: Failure responding to request: StatusCode=403 -- Original Error: autorest/azure: Service returned an error. Status=403 Code="RequestDisallowedByPolicy" Message="Resource 'rg-production-001' was disallowed by policy. Policy: 'Enforce-CostCenter'."
Scenario B: The Unsupported Resource
Plaintext
Error: creating Private Endpoint: Network.PrivateEndpointsClient#CreateOrUpdate: Failure sending request: StatusCode=400 -- Original Error: Code="NoTagsAllowed" Message="The resource type 'Microsoft.Network/privateEndpoints' does not support tagging."
The Cause: Timing & Scope
- For Scenario A (Policy): If you are using an older version of the AzureRM provider, or if you rely on
null_resourceto apply tags post-creation, the ARM API sees a creation request without tags. The Policy Gate we built in our previous article slams the door shut immediately. - For Scenario B (Unsupported): You likely defined
default_tagsin your mainprovider "azurerm"block. Terraform attempts to apply these tags to every resource it touches. When it tries to stamp aCostCentertag onto a resource that doesn’t have a tags schema (like a sub-resource), Azure rejects the malformed request.
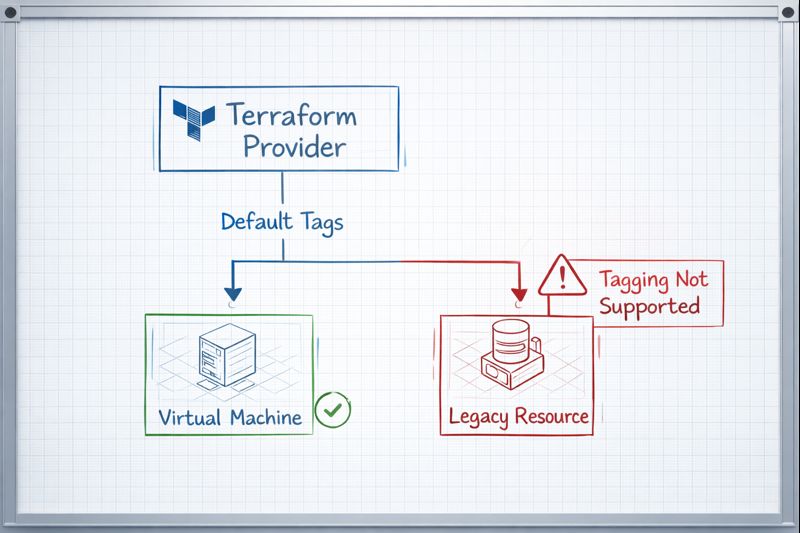
The Fix: The lifecycle Block
You don’t need to delete your global tags. We need to explicitly instruct the Terraform state engine to suppress drift detection for tags on these specific incompatible resources.
Fix for Scenario A (Policy Deny):
You must move the tags inside the resource block so they are sent in the initial PUT request.
Terraform
resource "azurerm_resource_group" "production" {
name = "rg-production-001"
location = "eastus"
# MANDATORY: Must be inline to pass Policy Gate
tags = {
CostCenter = "IT-Ops-101"
Env = "Production"
}
}
Fix for Scenario B (Unsupported Resources):
Use the ignore_changes lifecycle argument. This tells Terraform: “I know the provider wants to tag this, but please don’t.”
Terraform
resource "azurerm_private_endpoint" "example" {
name = "pe-example"
location = azurerm_resource_group.example.location
resource_group_name = azurerm_resource_group.example.name
subnet_id = azurerm_subnet.example.id
# ... other config ...
# THE FIX: Prevent default_tags from breaking this resource
lifecycle {
ignore_changes = [tags]
}
}
Decision Framework: Policy vs. Code
| Strategy | Speed | Safety | Context |
Provider default_tags | Fastest. One line covers 90% of resources. | Medium. Will break on unsupported resources (requires the fix above). | Best for general OpEx tracking. |
| Explicit Resource Tags | Slow. Requires verbose code in every block. | High. Granular control; passes strict Policy gates easily. | Best for Critical Prod infra. |
| Azure Policy Remediation | Slowest. Fixes tags after deployment. | Low. Resources exist untagged for minutes/hours (Governance Gap). | Best for Brownfield cleanup. |
Architect’s Note: If you rely on “Remediation Tasks” (fixing tags after creation), you are leaking money. The billing meter starts the millisecond the resource is created. If it runs for an hour without a tag, that’s an hour of attribution data lost forever.
External Research
This architectural deep-dive contains affiliate links to hardware and software tools validated in our lab. If you make a purchase through these links, we may earn a commission at no additional cost to you. This support allows us to maintain our independent testing environment and continue producing ad-free strategic research. See our Full Policy.