Terraform Is Not Infrastructure as Code — It’s Infrastructure as State: Here’s the Real Model
The biggest lie we tell junior engineers is that Terraform is a compiler. We hand them a .tf file and say, “This is the infrastructure.”
It isn’t.
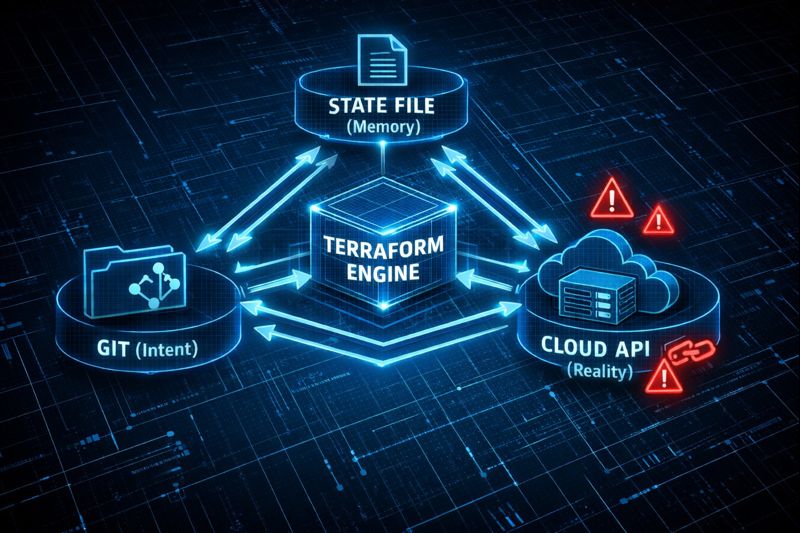
If Terraform were truly “Infrastructure as Code,” then the code would be the source of truth. But anyone who has operated a real cloud environment—especially one with multiple teams, incident pressure, and legacy systems—knows that the code is only Intent. The state file is Memory. And the cloud API is Reality.
The first time I saw a clean Git repo, a green pipeline, and a production VPC that looked like it had been through three different admins and a fire drill, I stopped calling Terraform “Infrastructure as Code.” The code said the security group was locked down. The state file said it was locked down. But the AWS console showed a rogue 0.0.0.0/0 rule added by a desperate developer at 2 AM.
Terraform didn’t fail. It just didn’t know.
Terraform isn’t a compiler. It’s a state engine that happens to accept code as input. If you don’t treat state as a first-class system, you’re not managing infrastructure—you’re writing fiction in HCL.
Key Takeaways
- Code is Just Intent: Treating Terraform as “code-only” creates invisible drift and security risk.
- The Three-Way Truth: Infrastructure exists in three simultaneous realities: Git (Intent), State (Memory), and the Cloud API (Reality).
- Governance via State: You must structure pipelines around refresh, signed plans, and state integrity—not just linting HCL.
Terraform Is an Infrastructure State Machine, Not a Compiler
Terraform builds a directed acyclic graph (DAG) by comparing what it remembers (state) with what you want (code). Only after that does it check the cloud.
Most teams operate on a flawed two-way mental model:
Git ↔ Cloud
They assume that if they change Git and push, the cloud updates accordingly. In reality, there’s a massive, fragile middle layer:
Git (Intent) ↔ State (Memory) ↔ Cloud API (Reality)
And that middle layer—the state file—is what actually controls the operation. Terraform cannot see anything it doesn’t track in state. This is where most teams get burned.
I once audited a client that believed their tagging policies were “enforced in IaC.” In reality, half their EC2 fleet had been created via ClickOps years before Terraform was adopted. Those resources were never imported. The HCL looked beautiful. The policies looked compliant. But Terraform simply ignored those resources—because they didn’t exist in state.
The result? $15,000/month in untagged, unallocated spend that “Infrastructure as Code” couldn’t see.
The Three-Way Integrity Model: Git, State, Cloud API
If you want deterministic infrastructure, you need to operate on a three-way integrity model:
- Git ↔ State: Does your intent match Terraform’s memory?
- State ↔ Cloud: Does Terraform’s memory match reality?
- Git ↔ Cloud: Only meaningful if the other two are clean.
This is the foundation of deterministic IaC pipelines and signed Terraform plans—because a signed plan is only a valid contract if the underlying state reflects reality at the time it was generated. If you skip State ↔ Cloud reconciliation (by disabling refresh or ignoring drift), your pipeline is effectively flying blind.
terraform plan by default checks Git ↔ State. It does not guarantee State ↔ Cloud unless you explicitly enforce refresh and drift detection.
Drift Handling: Stop Treating Code as the Source of Truth
Drift is not an error. It’s operational reality. The moment you deploy, entropy begins. Senior architects don’t treat drift as a cleanup task—they treat it as a first-class governance signal.
Operational Strategy: Containment Before Migration
When drift is detected, don’t immediately rush to “fix the code.” Start with state-first triage:
- Refresh-only plan:
terraform plan -refresh-only -detailed-exitcode - Decision gate:
- Import: Valid resource, missing from state.
- Recreate: Configuration drift, let Terraform overwrite.
- Ignore: Legacy brownfield, explicitly document and tag.
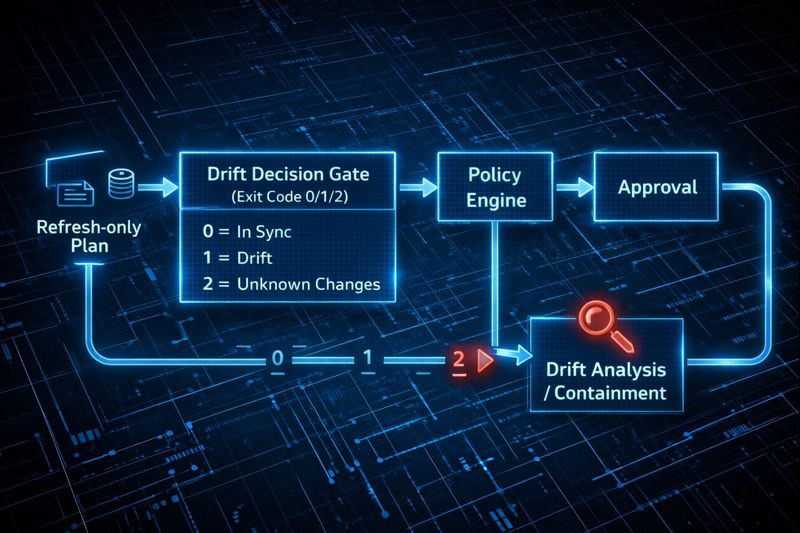
This turns terraform plan from a deployment step into a governance radar. If you want to close the console gap and use refresh-only as a drift radar, this becomes your early warning system—not your post-incident cleanup.
Architect’s Note: Stop using exit code 0 for everything. In our pipelines, exit code 2 triggers a dedicated Drift Analysis branch. It’s not a failed build—it’s a policy alert.
Policy as Code Only Works If Your State Is Honest
We love tools like OPA, Sentinel, and AI policy agents. But here’s the uncomfortable truth: Policy engines evaluate plans and state—not the raw cloud.
If your state is stale or incomplete, your policy is enforcing rules against a partial universe. I’ve seen CIS-aligned Terraform policies proudly enforced in pipelines while a legacy subnet with global access sailed underneath—because it never existed in state. The policy agent passed it. Not because it was compliant—but because it was invisible.
To fix this, you need layered guardrails: policy engines that evaluate plans and state, and inventory systems (AWS Config, CSPM, AI policy agents) that cross-reference live reality and flag what Terraform can’t see. Policy without state integrity is governance theater.
Where the CISO and CFO Get Nervous: Phantom Infrastructure
This isn’t just an engineering problem—it’s a risk and finance problem.
- Security Risk: Unmanaged security groups are one of the easiest entry points for attackers. Drift creates an attack surface you don’t even know exists.
- FinOps Risk: You cannot optimize what isn’t in your state file. Ghost resources break cost attribution, destroy TCO models, and inflate OpEx without accountability.
- Compliance Risk: State blind spots hide non-compliant architectures—data residency violations, segmentation failures, or shadow networks—especially dangerous in regulated or sovereign environments.
Drift tolerance is not an engineer convenience. It’s a governance decision.
Runbooks for a State-First Terraform Practice
If you want to move from “Terraform as scripting” to “Terraform as engineering,” adopt these patterns.
1. State Lifecycle Design
Never use local state. Ever. Use remote backends with locking (e.g., S3 + DynamoDB, GCS, Azure Storage). Apply stricter IAM to state storage than to production accounts. The state file holds the keys to the kingdom.
2. Workspace & Repo Topology
Align state files with blast radius, not convenience. Never mix prod and dev in the same state. One corrupted state file should cost you a microservice—not an entire region.
3. Drift SLAs
Define how quickly drift must be investigated in prod vs non-prod. Treat drift as an incident class, not a backlog item.
4. Change Contract Enforcement
Every apply must use a saved plan (-out=tfplan). Hash and sign the plan. Never apply a fresh calculation in prod—only a reviewed contract.
Terraform Usage Models: The Senior Architect’s View
| Dimension | Code-Only Mental Model | State-First Mental Model |
| Source of Truth | Git repo is assumed to be everything | Git + Accurate Remote State + Live API |
| Drift Detection | Best-effort, manual plan runs | Automated -refresh-only -detailed-exitcode gates |
| Policy Enforcement | HCL and modules only | Plans, State, and Drift outputs |
| Phantom Infra Risk | High — legacy and ClickOps invisible | Managed — import/ignore decisions documented |
| Who Gets Paged | Individual engineer (often ignored) | Platform team via defined Drift SLAs |
Final Thought
Terraform is not lying to you. You’re lying to yourself if you think code is reality.
Terraform is an infrastructure memory engine. If you treat its memory with the same rigor you treat your code—versioning it, protecting it, validating it against reality—you get deterministic infrastructure. If you don’t, you get a green pipeline, a clean repo, and a production environment that looks like it’s been through three different admins and a fire drill.
Additional Resources
- HashiCorp: Drift Detection and Refresh-Only Plans
- Google Cloud: Managing Infrastructure as Code with Terraform
- AWS: Best Practices for Terraform State
This architectural deep-dive contains affiliate links to hardware and software tools validated in our lab. If you make a purchase through these links, we may earn a commission at no additional cost to you. This support allows us to maintain our independent testing environment and continue producing ad-free strategic research. See our Full Policy.