Logic-Gapping Your Data: Engineering “Air Gaps” in a Zero-Trust World

Let’s just say it: the air gap is over.
Back in the day, “air gap” meant Dave tossed a tape in his truck and hauled it to some bunker in the mountains. It worked. It was also painfully slow. Now everyone wants a 15-minute RTO. Good luck getting a truck up a mountain that fast.
So we wired everything up. Backups plugged into the network. Tied straight into vCenter. Managed from shiny cloud dashboards. We got speed—and lost the gap.
Now when ransomware shows up, it’s not just encrypting files. It’s riding your management network. Using your own admin creds to stroll into the backup console, flip off immutability, delete your recovery points, wipe the whole catalog.
We can’t just unplug things anymore. So what do we do? We break trust instead.
Welcome to the Logic Gap.
Why VLANs Don’t Cut It
Let’s stop telling auditors we’ve got an air gap because our backup server sits on a different VLAN. That’s segmentation. It’s not isolation.
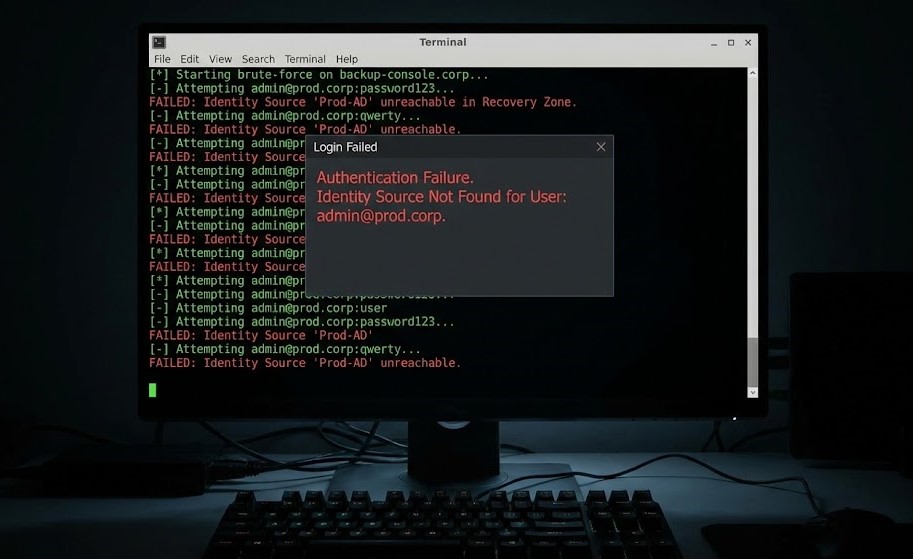
If your backup environment uses production Active Directory for logins, you’ve got no gap. If someone pops a Domain Admin in production, they own everything—file servers, backup boxes, storage arrays, even your so-called “immutable” silos.
Modern ransomware doesn’t smash its way in. It just logs in.
A real Logic Gap demands Identity Isolation. Your recovery environment has to run under its own identity authority—not a different OU, but a totally separate AD forest, a separate IdP, or no domain at all. No shared accounts. No trust relationships. No overlapping MFA tokens. If production burns down, the Vault shouldn’t even recognize a production credential.
The Modern Ransomware Chain: How Backups Really Die
Here’s how it actually goes down:
- Initial Access: An attacker gets in—phishing, VPN exploit, exposed RDP.
- Lateral Movement: They move laterally using Active Directory.
- Credential Theft: They steal credentials—Domain Admin, backup admin, anything useful.
- Admin Access: They log into backup consoles and storage management planes.
- Destruction: They delete snapshots, disable immutability, wipe catalogs.
- Encryption: They encrypt production—and now there’s nothing left to recover.
Notice what’s missing? Nobody’s brute-forcing storage. They’re authenticating into it.
The Logic Gap exists to break the chain at step four—where production credentials simply stop working.
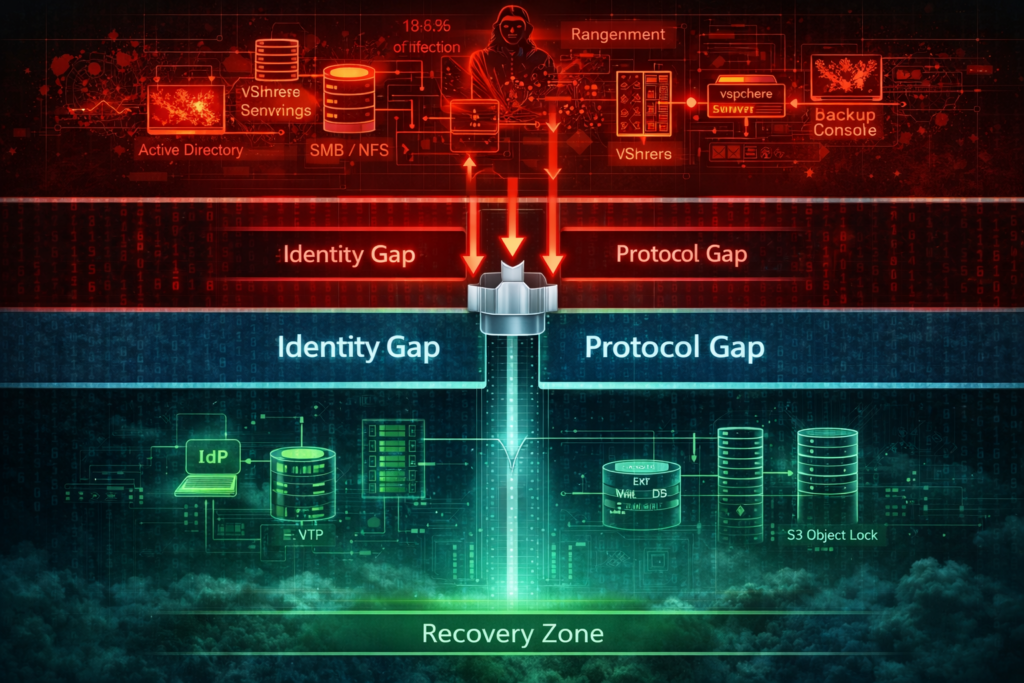
Building the Logic Gap
This isn’t about buying a product. It’s about data protection architecture—and it rests on three severances.
1. Identity Severance
The Recovery Zone—your Vault—must operate under a separate identity authority. That could be a distinct AD forest, a different IdP, or a standalone workgroup. No domain joins. No trust relationships. No shared accounts. Production credentials do not exist here. If Prod goes up in flames, the Vault doesn’t care.
2. Protocol Severance
Ransomware thrives on discoverable protocols—SMB, NFS, iSCSI—anything it can scan, mount, or enumerate. A Logic Gap relies on API-driven, non-browsable interfaces like S3 Object Lock, Catalyst, or other write-once protocols. Data moves, but attackers can’t explore. No mount points to scan. No shares to traverse. No directories to crawl.
3. Management Plane Severance
Recovery systems must not be manageable from the normal IT network. Consoles should require a jump box, a physically isolated management plane, or out-of-band access. If someone owns your production jump host, they still shouldn’t be able to touch the Vault. That’s what creates a real, software-defined air gap.
Living with the Logic Gap: Access Control vs. Access Paralysis
Logic Gaps make life harder. That’s the point.
If it’s easy for you to delete a snapshot, it’s easy for an attacker. You’re trading convenience for survival.
But that creates a new risk: Access Paralysis.
During an attack, your usual tools—DNS, AD, RDP, SSO—may be unavailable. If your Logic Gap relies on those same services, you’ve locked yourself out of your own lifeboat.
That’s why drills matter. As we said in RTO Reality, a backup doesn’t count until you restore it. A Logic Gap doesn’t count until you cross it while production is dark. If you can’t reach your Vault during a simulated attack, your Logic Gap is cosmetic—not architectural.
The Verdict: Build the Wall
We can’t go back to tapes in trucks. The data gravity is too high.
Our air gap is now software-defined—enforced by identity architecture, protocol selection, and management plane isolation. It is fragile. A single misconfigured firewall rule or a lazy domain join can collapse it instantly.
Build the wall. Sever the identity. Isolate the protocol.
If you don’t logic-gap your data, you’re not building resilience—you’re building a centralized deletion console for the attacker.
External References & Further Reading
- NIST SP 800-61r2 – Computer Security Incident Handling Guide
- NIST SP 800-53 – Security and Privacy Controls for Information Systems
- CISA – Ransomware Guide
- MITRE ATT&CK – Impact Tactics (Data Destruction, Service Stop)
Editorial Integrity & Security Protocol
This technical deep-dive adheres to the Rack2Cloud Deterministic Integrity Standard. All benchmarks and security audits are derived from zero-trust validation protocols within our isolated lab environments. No vendor influence.
This architectural deep-dive contains affiliate links to hardware and software tools validated in our lab. If you make a purchase through these links, we may earn a commission at no additional cost to you. This support allows us to maintain our independent testing environment and continue producing ad-free strategic research. See our Full Policy.