Backups Are Compromised First: Inside Cohesity FortKnox and the Rise of Cyber Vaulting
Backups: The First Thing Hackers Go After
For years, backup strategy felt like an engineering debate. We obsessed over dedupe ratios, throughput, and how fast we could recover—all built on one big assumption: when production failed, backups would still be safe.
Ransomware shattered that idea.
Hackers don’t treat backups as an afterthought anymore. They aim for them first. These days, attacks often play out quietly over weeks. Attackers comb through backup catalogs, steal admin credentials, tamper with snapshots, and mess with retention settings long before they hit encrypt. By the time you realize you need to recover, the attacker has already decided what “recovery” actually means.
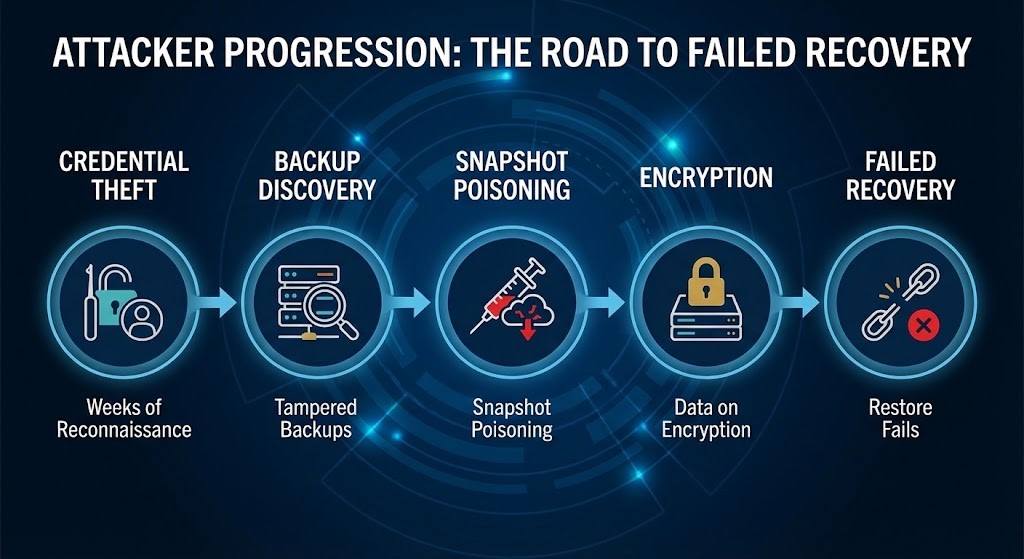
So now, it’s not just about recovering at all. It’s about trusting what you recover.
Enter Cohesity FortKnox on Google Cloud.
This isn’t just another backup tool, it draws a hard line between backup infrastructure and recovery authority.
The Industry Finally Admits the Problem
Ransomware incidents exposed a nasty truth: you could restore your environment perfectly… and get reinfected right away.
Attackers go after identity systems first. Once they grab admin authority, “immutable” storage and retention locks don’t mean much if the admin keys are compromised. The attacker decides what gets written long before you even know something’s wrong.
As we argued in Immutability Is Not a Strategy, the problem wasn’t the storage. The problem was trust.
So, What Is FortKnox?
People call FortKnox a cyber vault. Really, it’s a separate recovery zone.
Instead of just toughening up backups, it pulls recovery authority out of your compromised environment. The vault keeps immutable copies of your data in a place your usual admins can’t reach on their own.
That’s a big deal:
- Backups just protect your data from being deleted.
- A Vault protects the whole recovery process from people who shouldn’t have control.
Why Google Cloud?
It’s not just about scale. It’s about having a separate control plane.
Most offsite backups still share identity providers or automation with the main environment. Attackers know this—and they use it. This creates what we call a “logic gap” failure (see: Logic-Gapping Your Data).
By running FortKnox in a totally separate security domain, you force recovery to go through checks and approvals. The cloud isn’t just another storage spot; it’s a neutral ground for recovery, outside the blast radius.
How It All Works
Backups move into the vault only during set transfer windows. Outside those times, production systems can’t touch it. Even your admins can’t just poke around in there.
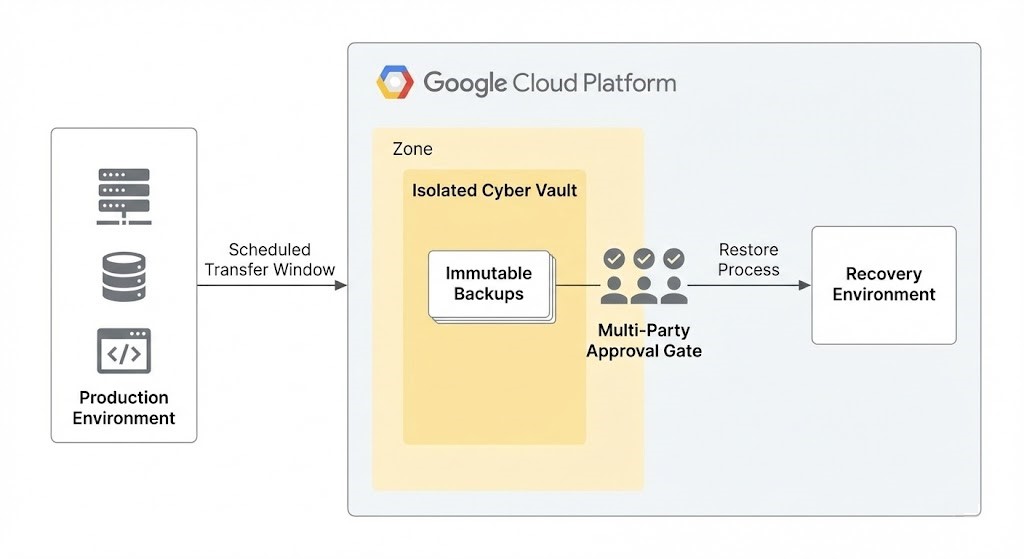
When you need to recover, one person can’t do it alone. You need multiple, independent approvals. Only then does the system spin up a temporary recovery setup, where you validate the data before using it.
That validation? It’s the heart of the whole thing. You’re not just restoring files. You’re restoring a clean slate.
What Do You Actually Get?
This isn’t about faster recovery. In fact, due to the Physics of Data Egress, it might even feel mechanically different than a local restore. But it’s about peace of mind.
You get confidence that hackers never touched the last good backup. You’re protected from stolen credentials and rogue insiders. You have proof for auditors and cyber-insurance claims. Most of all, when the execs ask, “Are we sure this environment is safe?” — you can finally give a real answer.
Failure Modes: What This Actually Protects You From
People usually talk about backup by listing off features, but when you’re thinking about recovery architecture, what really matters is: how do you survive a worst-case scenario?
Here’s where things get real. The difference between a hardened backup and a true vault shows up when an attacker already has admin rights. Let’s say someone cracks a domain administrator account. Regular backup systems still trust that account they’re tied into the same identities you use for production. At that point, your so-called “immutable” backups only protect the data that’s already there. Nothing stops an attacker from quietly corrupting every new backup, making sure every restore point is tainted. A vault dodges this trap because it handles recovery authorization outside the compromised identity system.
Now, what if someone compromises your backup admins? Most backup platforms still let someone mess with things like retention periods, replication, or configuration all ways to destroy or sabotage backups without actually deleting files. With a vault, you need independent approval from people or identities completely outside the hacked environment. The attacker might know the vault exists, but they can’t use it.
Insiders are a similar story. A privileged employee can do real damage, but they can’t greenlight a recovery all on their own. The whole idea is to assume authority itself could go bad, not just make a mistake.
Then there’s the slow-burn ransomware. Attackers often wait out your backup rotation, so by the time you realize something’s wrong, every backup looks clean but is actually compromised. Clean-room validation helps by stopping you from just reinstalling compromised accounts or scheduled tasks straight back into production.
Corrupted snapshots are sneakier. Backup software will happily restore everything even if that means putting back broken configs, poisoned group policies, or hidden persistence tools. From a technical standpoint, the restore “succeeds,” but you’re just putting the infection right back. A vault treats restoration as an investigation, something you examine closely before you roll it out.
At the end of the day, it’s straightforward: traditional backup protects your data’s integrity. A vault protects the integrity of your recovery decisions.
Different Solutions, Different Problems
The real differences in the market are philosophical rather than feature-based.
| Capability | Cohesity FortKnox | Rubrik | Veeam Software |
|---|---|---|---|
| Design Goal | Independent recovery authority | Harden backup platform | Flexible recovery orchestration |
| Core Assumption | Assume breach | Prevent breach | Recover quickly |
| Isolation Method | Managed cyber vault | Logical air-gap & zero trust | Hardened repository patterns |
| Admin Compromise Protection | Very strong | Strong | Depends on architecture |
| Recovery Validation | Built-in clean room validation | Detection & monitoring | Manual validation |
| Operational Complexity | Low (managed) | Medium | High (DIY design) |
| Recovery Speed | Slower but trustworthy | Balanced | Fastest |
| Ideal Use Case | Compliance & high-risk environments | Security-mature organizations | Operational IT-centric teams |
The important takeaway is that these are not direct replacements for one another.
They solve different failure scenarios.
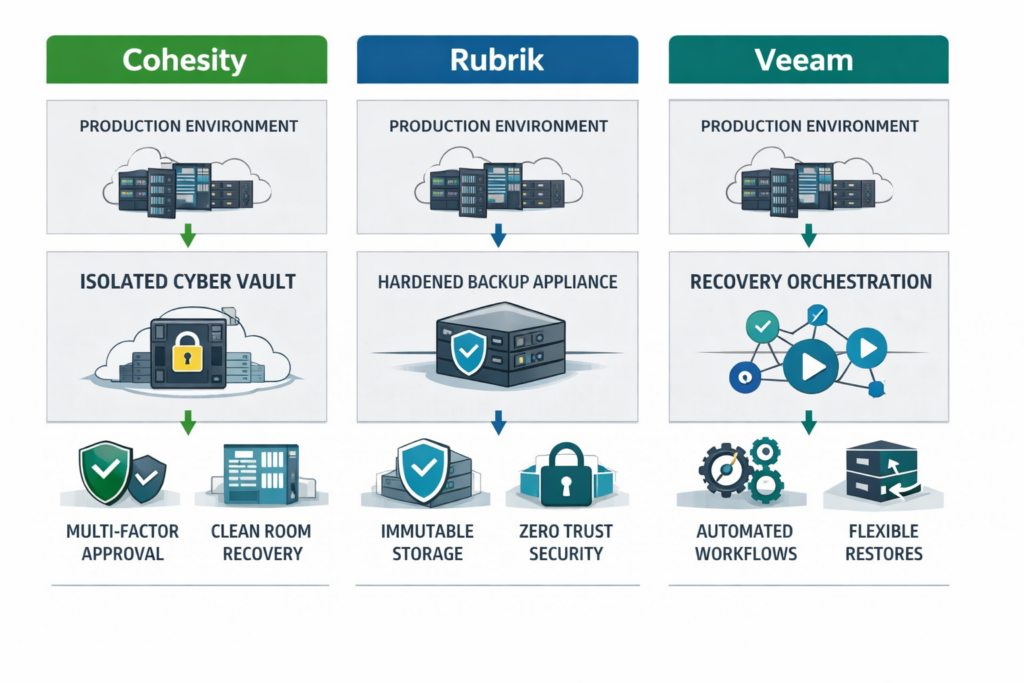
- Rubrik works to protect the backup system itself.
- Veeam zeroes in on controlling the workflow for recovery.
- FortKnox is all about separating trust from anything that’s been compromised.
(For a deeper dive on how these compare, review our analysis on Ransomware Recovery Metrics.)
When Does This Make Sense?
You want this setup when restoring bad data could be a disaster. If your environment holds identity systems, financial records, or regulated data, you can’t risk letting attackers sneak back in during recovery.
Smaller shops, short-lived workloads, or setups you can rebuild from code probably don’t need the extra steps. Hardened backups are enough there. It’s not about how much data you have. It’s about how much risk you’re willing to accept.
The Tradeoff: Safety Over Speed
Cyber vaulting slows things down on purpose.
Traditional disaster recovery is about getting back online fast. Vault recovery is about making sure you’re safe before anything else. You can’t have both at the same time, and this architecture always picks safety first.
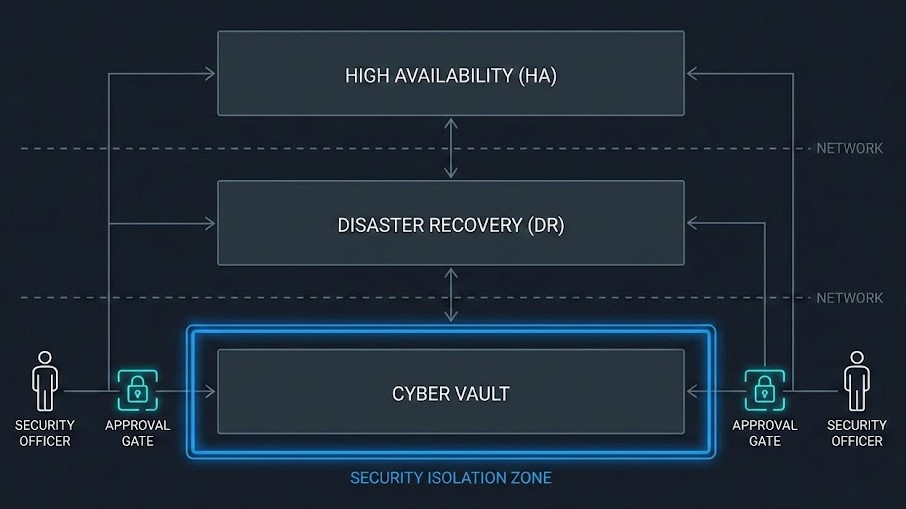
Think of resilience in layers:
| Layer | Purpose |
|---|---|
| High Availability | Handle outages |
| Disaster Recovery | Handle infrastructure loss |
| Cyber Vaultulting | That’s for when an attacker already has the keys. |
FortKnox is built for that last scenario. That’s where it matters.
Cost Is About Assurance, Not Capacity
Organizations evaluating vault cost as storage pricing often misunderstand the purchase. The primary value is not retention or replication — it is defensible recovery integrity.
The economic comparison is less against object storage and more against breach investigation cost, legal exposure, and downtime credibility. In many deployments, security and risk teams justify the platform more than infrastructure teams.
The Industry Shift This Represents
Backup historically answered: Can we restore?
Cyber vaulting answers: Should we trust what we restored?
That distinction signals a structural change in enterprise architecture. Availability is no longer sufficient. Recovery must also be provable.
Final Takeaway
For decades recovery planning assumed failure was accidental. Modern recovery planning assumes failure is adversarial.
FortKnox does not replace backup software or disaster recovery. It replaces an assumption – the assumption that backups remain trustworthy after a breach.
And once that assumption disappears, a new architectural layer becomes necessary: a recovery authority outside the compromised system. That is the cyber-vault era.
Additional Resources
For architects validating this strategy, we recommend the following primary sources:
- NIST SP 800-209 (Security Guidelines for Storage Infrastructure): The definitive standard for securing storage and backup planes against compromise.
- Cohesity FortKnox on Google Cloud: Official architecture documentation and capability set.
- CISA #StopRansomware Guide: Federal guidance on isolating backups and the “3-2-1” rule in the modern threat landscape.
- Backup Architecture and Data Integrity
- Disaster Recovery Logic
Editorial Integrity & Security Protocol
This technical deep-dive adheres to the Rack2Cloud Deterministic Integrity Standard. All benchmarks and security audits are derived from zero-trust validation protocols within our isolated lab environments. No vendor influence.
This architectural deep-dive contains affiliate links to hardware and software tools validated in our lab. If you make a purchase through these links, we may earn a commission at no additional cost to you. This support allows us to maintain our independent testing environment and continue producing ad-free strategic research. See our Full Policy.






