The New Sovereign Cloud Era — What European AWS Cloud Means for Global Architecture
This strategic advisory has passed the Rack2Cloud 3-Stage Vetting Process: Market-Analyzed, TCO-Modeled, and Contract-Anchored. No vendor marketing influence. See our Editorial Guidelines.
Key Takeaways:
- It’s a Partition, Not a Region: The AWS European Sovereign Cloud (
aws-eusc) is a hard fork. It has its own IAM, billing, and DNS root. It shares nothing witheu-central-1. - The “Service Gap” is Real: Launching with only ~90 services means common staples like CloudFront and Amplify are currently missing. You cannot just “deploy to Brandenburg”.
- The OpEx Shock: Expect a 20–30% operational tax. You are not just paying for instances; you are paying for duplicated CI/CD pipelines, separate staffing, and a disconnected observability stack.
- Sovereignty ≠ Immunity: Even with this launch, major industrial players remain skeptical about true legal immunity from the US CLOUD Act. Use it for compliance, not for geopolitics.
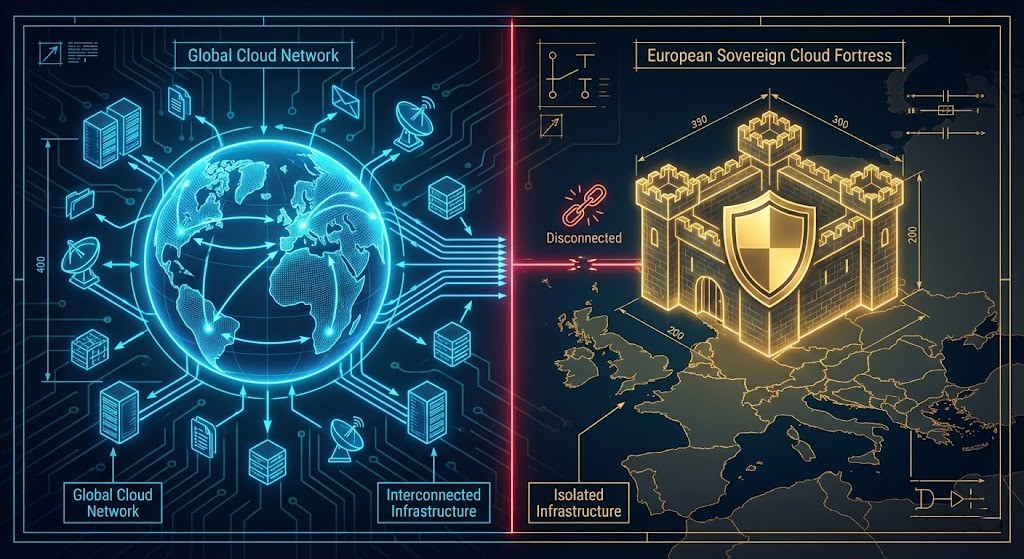
The End of the Borderless Cloud
I still remember a migration in 2012—standing in a freezing London data center, trying to explain to a bank CIO that “the cloud” didn’t mean his data would float freely over the Atlantic. Back then, we sold the vision of a borderless control plane. One global identity. One billing engine. One operational universe.
We weren’t lying—but we were definitely naive.
Last week’s launch of the AWS European Sovereign Cloud in Brandenburg, Germany marks the formal end of that era. This is not a new region you casually select in a dropdown. It is a hard fork of cloud architecture—legally, operationally, and technically.
For the last decade, compliance was often a checkbox: “Just use eu-central-1 and encrypt everything.”
That approach is dead. With confirmed launch customers like EWE AG and Sanoma Learning moving workloads into physically isolated racks, the bar has moved. It is no longer about Data Residency (where the bits live). It is about Operational Sovereignty—who holds the keys, who patches the hypervisor, and whose passport they hold.
It’s Not a Region. It’s a Partition (aws-eusc)
To design this correctly, you must understand the physics of the environment. This is a “Shared Nothing” partition—architecturally identical to the US GovCloud model.
In a standard AWS deployment:
- IAM is global.
- Billing rolls up to a US master payer.
- DNS relies on global Route 53 zones.
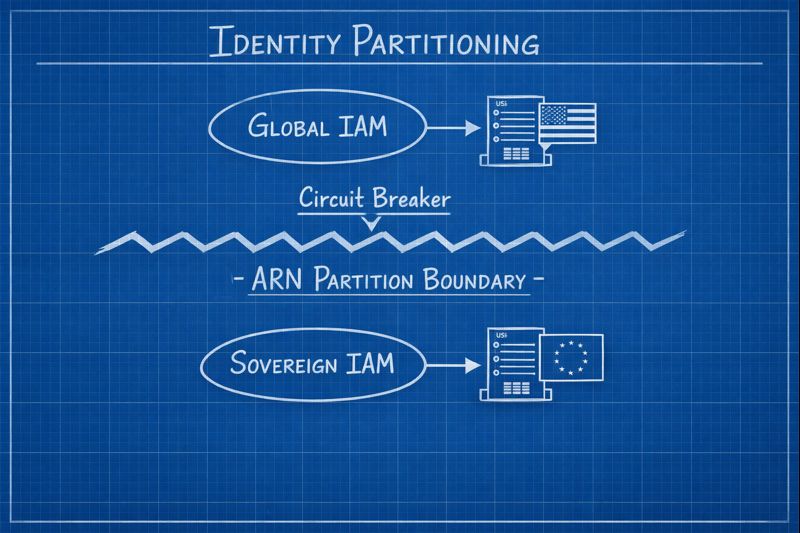
In the Sovereign Cloud (aws-eusc), that umbilical cord is cut:
The Partition Impact Matrix
| Feature | Standard AWS (eu-central-1) | AWS Sovereign Cloud | Architectural Impact |
| Control Plane | Global | EU-resident, EU-citizen operated | No global failover; separate pipelines required. |
| Identity (IAM) | Global | Isolated Partition | No direct role federation. arn:aws:iam vs arn:aws-iso:iam mismatch. |
| Billing | Aggregated | Separate Legal Entity | FinOps tooling must consolidate multiple invoices. |
| Connectivity | AWS Backbone | Dedicated EU Connectivity | Feels “air-gapped”; requires dedicated interconnects. |
The Architect’s Warning: If your Terraform scripts assume global IAM roles, or if your web app relies on CloudFront (which is currently not available in the sovereign partition), your deployment will fail. Not degrade. Fail.
The Sovereignty Tax: Where the Real Cost Lives
Most organizations obsess over instance pricing (OD vs RI). That is the wrong place to look. The real cost of the Sovereign Cloud is in Operations.
I recently modeled a sovereign migration for a defense contractor. Their biggest shock wasn’t the EC2 premium—it was that their US-based Datadog and PagerDuty instances became legally unusable for the sovereign environment. Metadata could not leave the EU partition.
The Hidden Costs:
- Tooling Duplication: You need a separate CI/CD control plane. You cannot push to
aws-euscfrom a runner inus-east-1without breaking the legal air gap. - Brain Drain: AWS restricts support access to EU residents. If your best database architect is in Seattle, they legally cannot touch production. You must hire duplicate senior talent inside the Eurozone.
- The “Missing Service” Tax: No Amplify? No CloudFront? You are now engineering your own CDNs and static hosting solutions like it’s 2015.
Architect’s Action: Before committing, you must model this OpEx bloat. Use our Cloud ROI Estimator to compare “Global Operations” labor vs. “Sovereign” labor. If the premium exceeds 30%, challenge the compliance team to cite the exact regulation mandating the move.
Data Gravity Becomes Geopolitical Gravity
Here is the irony: In escaping US jurisdictional lock-in, you accept geopolitical lock-in.
Once data enters the aws-eusc partition, egress is technically easy but legally treacherous. AI training pipelines that assume global data lakes break when datasets cannot legally leave the partition.
The “Airbus” Lesson: While many are celebrating, it is telling that Airbus—arguably the target audience for this cloud—has publicly expressed skepticism about whether any US-owned cloud can truly offer immunity from the US CLOUD Act.
This proves the point: Sovereign Cloud is a compliance tool, not a magic shield.
Decision Framework: Do You Actually Need It?
Zone A — Must Move (aws-eusc)
- Data: NIS2 High Criticality, National Defense, Health Data with strict localization.
- Mandate: Explicit requirement for “Operational Sovereignty” (EU-only staff).
Zone B — Stay Standard (eu-central-1)
- Data: Standard GDPR PII, Commercial IP.
- Need: Full AI portfolio, CloudFront/Edge services, Global Interconnectivity.
If your justification lives in Zone B, moving to the Sovereign Cloud is an unforced error. You are trading agility for a compliance badge that your regulator didn’t ask for.
Conclusion: Architecting for a Split World
The “one cloud” era is over. Modern architects must design for a world where systems span legally distinct cloud partitions. Your job is no longer just optimizing for latency or throughput. You are now optimizing for jurisdiction.
That means abstracting identity providers, designing automation for multi-partition deployment, and never assuming a service available in us-east-1 exists in eu-sovereign-1.
The Sovereign Cloud is a fortress. Just remember: Fortresses are excellent for defense — and notoriously hard to leave.
Additional Resources
- AWS European Sovereign Cloud Announcement (Source: AWS)
- NIS2 Directive Overview (Source: European Commission)
- Airbus Cloud Strategy (Source: Airbus)
- Rack2Cloud Deterministic Tools For A Non-Deterministic Cloud
This architectural deep-dive contains affiliate links to hardware and software tools validated in our lab. If you make a purchase through these links, we may earn a commission at no additional cost to you. This support allows us to maintain our independent testing environment and continue producing ad-free strategic research. See our Full Policy.