Azure Landing Zone vs. AWS Control Tower: The Architect’s Deep Dive
Same Destination, Different Vehicles
By now, the concept of a “Landing Zone” is well understood in the enterprise. It is the pre-configured, secure, and scalable foundation upon which workloads are deployed. It’s the antidote to the “wild west” of unmanaged cloud accounts and subscriptions.
For Solution Engineers and Architects working in multi-cloud environments, simply knowing that both AWS and Azure offer a landing zone solution isn’t enough. The fundamental differences in how they are architected, deployed, and managed have massive downstream implications for operational overhead, flexibility, and security posture.
AWS Control Tower is a managed service that acts as an opinionated orchestrator. Azure Landing Zones (specifically the Enterprise-Scale architecture) is a prescriptive architecture and methodology implemented via infrastructure as code.
This deep dive explores the mechanics beneath these two approaches.
1. The Core Philosophy: Service vs. Architecture
The most critical distinction lies in how the providers deliver the solution.
AWS Control Tower: The Prescriptive Service Control Tower is a product you “turn on.” It is highly opinionated, aimed at getting customers from zero to a baseline-governed state quickly. It acts as an abstraction layer sitting on top of AWS Organizations, CloudTrail, Config, and IAM Identity Center.
- Pros: Speed of deployment, standardized best practices out-of-the-box, simplified initial experience.
- Cons: Can feel like a “black box.” Customization outside its prescriptive path often requires add-on frameworks (like Customizations for Control Tower – CfCT – or Account Factory for Terraform – AFT), which increases complexity.
Azure Landing Zone (Enterprise-Scale): The Modular Architecture Azure doesn’t have a single “Control Tower” service button. Instead, it provides reference implementations (in Bicep and Terraform) of the “Enterprise-Scale” architecture. It’s a blueprint that you deploy.
- Pros: Incredibly flexible and modular. Because it’s essentially a complex set of IaC templates, you can modify the architecture to fit exact needs (though deviating from the blueprint requires expertise). It integrates natively with existing Azure DevOps or GitHub workflows.
- Cons: Higher initial learning curve. Requires a stronger grasp of core Azure concepts (Management Groups, Policy, RBAC) before deployment.
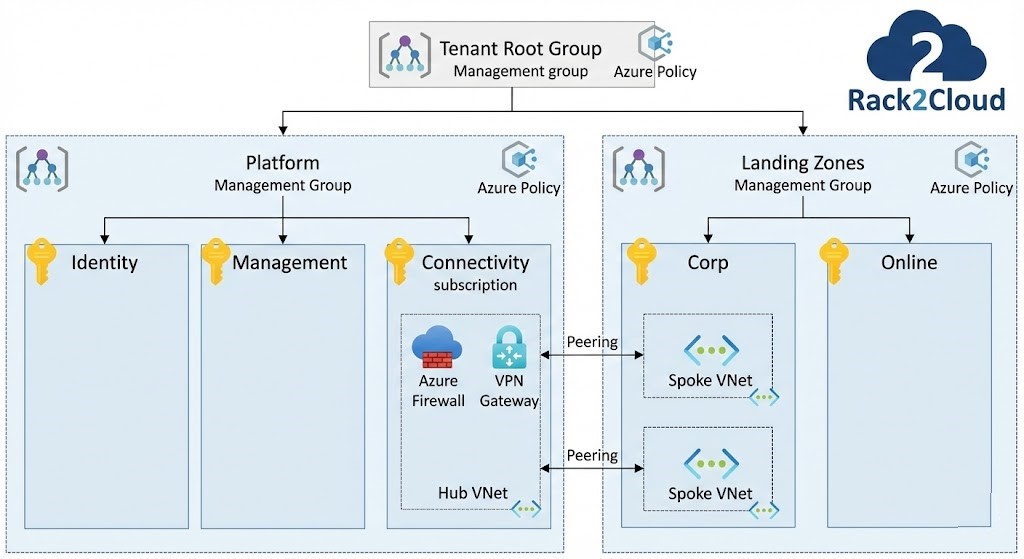
Image 1: Azure Enterprise-Scale Landing Zone Architecture. This diagram highlights the Management Group hierarchy for policy inheritance and the Hub-and-Spoke network topology.
2. The Skeleton: Hierarchy and Structure
How do we organize the sprawl?
Azure: The Power of Management Groups Azure’s secret weapon is the Management Group hierarchy. Unlike AWS Organizations which are often relatively flat, Azure encourages deep nesting designed specifically for policy inheritance.
- The Deep Dive: Azure separates the billing construct (Enterprise Agreement enrollment) from the organizational construct (Management Groups). The ALZ reference architecture dictates a specific hierarchy (e.g., “Corp” vs. “Online” management groups) to apply distinct policies to different workload types. Subscriptions live under these groups and inherit policies automatically.
AWS: Organizations and OUs AWS uses AWS Organizations and Organizational Units (OUs). Control Tower mandates a specific starting structure: A Security OU (for log archive and audit) and a Sandbox OU.
- The Deep Dive: While you can nest OUs deeply, AWS historically favored flatter structures. Control Tower’s rigidity means you must work within its defined OU structure for enrolled accounts. Moving accounts around after the fact, or integrating existing complex organizations, can sometimes break Control Tower’s orchestration guardrails.
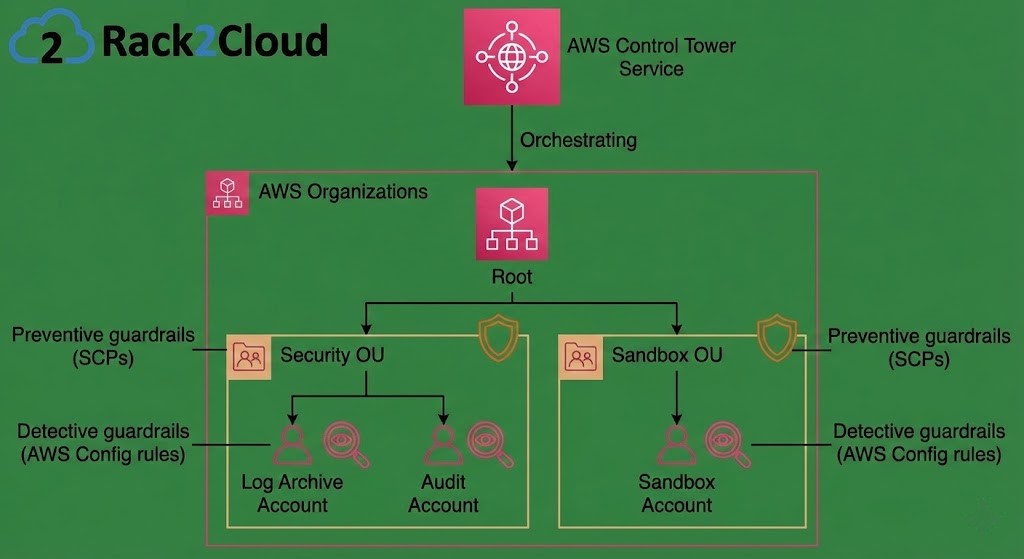
Image 2: AWS Control Tower Structure. This diagram shows the Control Tower service orchestrating AWS Organizations, the required OU structure, and the application of preventive and detective guardrails.
3. The Muscles: Governance and Policy Engines
This is where the technical differences become most pronounced and critical for SEs to understand.
Azure Policy: The Scalpel Azure Policy is arguably the most powerful governance engine in the public cloud.
- How it works: It sits directly at the ARM (Azure Resource Manager) API layer. Every request to create or modify a resource passes through Azure Policy first.
- Granularity: It is incredibly granular. You can enforce tags, restrict specific SKU sizes based on environment type, or mandate specific configurations inside a resource.
- Real-time Enforcement & Remediation: It can perform
Deny(blocking non-compliant deployments in real-time),Audit(flagging them),Append(adding required tags automatically), andDeployIfNotExists(remediating non-compliant resources automatically). - The Advantage: Because policies are applied to Management Groups, a single policy assignment can govern thousands of subscriptions instantly, even retroactively auditing existing resources.
AWS Control Tower: The Shield and The Camera (SCPs & Config) AWS uses a two-pronged approach that is generally less granular but effective for broad strokes.
- Service Control Policies (SCPs) – The Shield: These are the “preventive guardrails.” They act as a permission boundary on an AWS account. They are excellent at broad denials (e.g., “Deny access to unregistered regions,” or “Deny deleting CloudTrail logs”). However, they are coarse. An SCP cannot say “Enforce this specific tag value on an EC2 instance”; it can only say “Deny RunInstances if tags are missing.”
- AWS Config – The Camera: These are the “detective guardrails.” Config monitors resources after they are deployed. If someone deploys a non-compliant S3 bucket, Config detects the drift and alerts (or triggers a Lambda for remediation). There is a latency between deployment and detection.
The SE Takeaway: Azure Policy prevents bad configurations from ever happening with high granularity. AWS relies on broad preventive blocks (SCPs) combined with reactive detection (Config) for fine-grained issues.
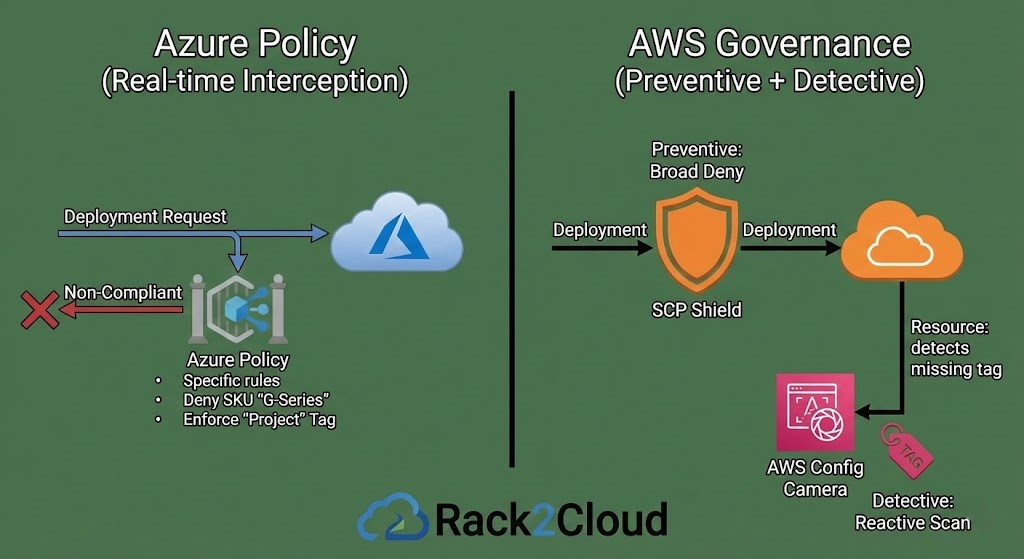
Image 3: Governance Engine Comparison. This diagram illustrates the fundamental difference between Azure Policy’s real-time interception and AWS’s combination of broad preventive shields (SCPs) and reactive detective scans (AWS Config).
4. The Nervous System: Networking Integration
Azure Landing Zone: Networking is deeply integrated into the ALZ architecture. The accelerators assume a Hub-and-Spoke model. It natively orchestrates the deployment of the Hub VNet, Azure Firewall, VPN Gateways, and ExpressRoute connections. It strongly pushes the use of Azure Virtual WAN (vWAN) for large-scale global deployments, making transit routing drastically simpler.
AWS Control Tower: Control Tower’s native networking is basic. It provisions VPCs in new accounts based on simple parameters. However, it does not natively orchestrate complex transit networking like AWS Transit Gateway (TGW) out of the box. To build a true Hub-and-Spoke in AWS, you usually need to leverage add-ons like AFT (Account Factory for Terraform) or build custom automation to handle TGW attachments and routing tables as new accounts are vended.
| Feature | Azure Landing Zone (Enterprise-Scale) | AWS Control Tower |
| Delivery Mechanism | Prescriptive Architecture (IaC blueprints) | Managed Service (Opinionated Orchestrator) |
| Primary Hierarchy | Management Groups (Deep nesting, inheritance focus) | AWS Organizations & OUs (Rigid initial structure) |
| Primary Policy Engine | Azure Policy (Granular, API-layer interception, real-time deny/remediate) | SCPs (Coarse preventive boundaries) & AWS Config (Reactive, granular detection) |
| Networking | Native Hub-and-Spoke / vWAN orchestration | Basic VPC provisioning. Complex transit usually requires add-ons (AFT/CfCT). |
| Customization | High (Modify the IaC directly) | Medium/Low (Requires extensions like CfCT or AFT) |
| Day-2 Operations | Managed via code (GitOps flow) | Managed via Console or Service Catalog (drift detection provided by service) |
Conclusion: Positioning Strategy for SEs
When guiding customers, avoid declaring one “better” than the other. They are fundamentally different approaches suited to different organizational DNA.
Position Azure Landing Zone when the customer:
- Needs highly granular, real-time policy enforcement (e.g., strict regulatory industries).
- Has a strong “Infrastructure as Code” maturity and wants to manage governance via GitOps.
- Requires complex, deeply nested hierarchies to map to their business structure.
- Is already heavily invested in the Microsoft ecosystem (AAD/Entra ID integration is seamless).
Position AWS Control Tower when the customer:
- Wants the fastest path to a baseline, best-practice multi-account environment.
- Prefers a managed service approach over maintaining complex IaC blueprints.
- Is comfortable with the “AWS way” of rigid initial structures and extending functionality through add-on frameworks.
- Needs broad-brush guardrails initially and will mature into fine-grained Config rules later.
Ultimately, both lead to the same destination: a governed cloud. The choice defines the operational journey they will take to get there.
Additional Resources
- WS Landing Zone
- AWS Ultimate Guide
- Microsoft Azure Landing Zone
- Azure Landing Zone:Practical Guide to Cloud Foundations
- Exam Ref AZ-900 Microsoft Azure Fundamentals
This architectural deep-dive contains affiliate links to hardware and software tools validated in our lab. If you make a purchase through these links, we may earn a commission at no additional cost to you. This support allows us to maintain our independent testing environment and continue producing ad-free strategic research. See our Full Policy.