Your Ransomware Plan Is Fiction: 5 Recovery Metrics Nutanix, Cohesity, Rubrik & Pure Can’t Hide
Every ransomware vendor demo shows a single VM booting in 60 seconds. Every real ransomware recovery looks like this: The backups are intact. The ransomware is neutralized. The executives are on the bridge. And nothing is coming back online. Recovery is not a software problem—it’s a physics problem. It is a war against bandwidth, IOPS,…
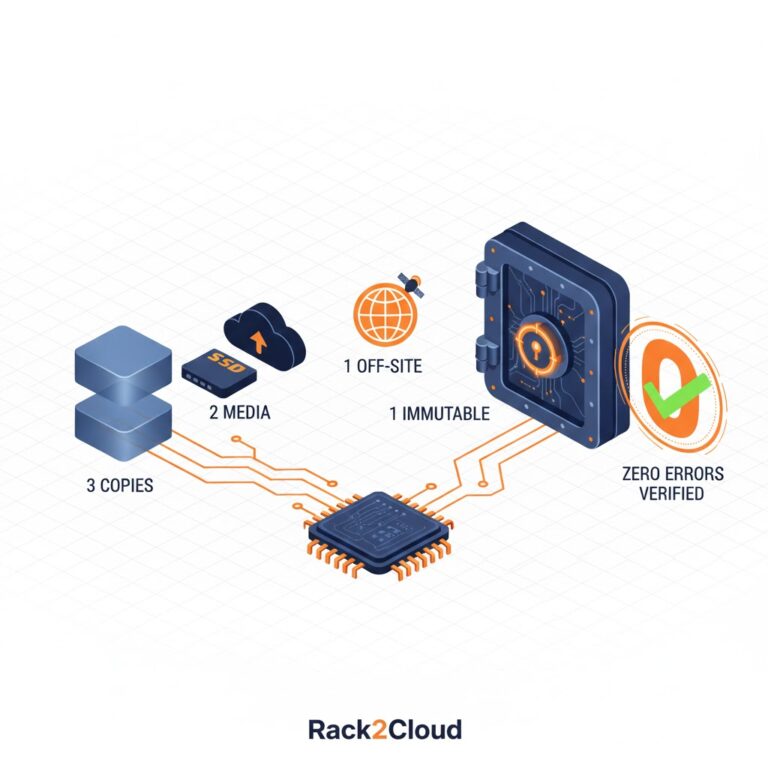
The 3-2-1-1-0 Rule: Modernizing Backup Protocols for 2026 Cyber-Resilience
The traditional 3-2-1 backup strategy was designed to solve for hardware failure; the 3-2-1-1-0 rule is engineered to solve for adversarial intent. In a landscape where 94% of ransomware attacks now specifically target the backup server, a “copy” is no longer a recovery asset unless it is cryptographically or physically isolated from the production plane….
Ransomware‑Ready Backup Strategy for 2025: What Every Engineer Must Know
In 2020, the advice was “have good backups.” In 2025, that advice is dangerously incomplete. Today, backup infrastructure is not the remediation; it is the primary target. Modern ransomware cartels know that if they encrypt your production data, you will restore. But if they delete your backups first, you will pay. Attackers now spend weeks…
The Indestructible Vault: How Veeam, Rubrik, and Cohesity Architect Immutable Backups
Introduction: The Day Your Backups Betrayed You It is the nightmare scenario every IT leader fears. You get the ransom note. Your primary servers are encrypted. You calmly turn to your backup console, ready to initiate a restore and be the hero. But the console is empty. Or the backup files are corrupted. Modern ransomware…
Download Your Architecture Playbooks - Select your infrastructure paths. Receive field-tested blueprints. SEND MY PLAYBOOK