KASLR + SMEP/SMAP: Measuring Real Attack Surface Reduction
In this field, we love to treat kernel flags like they’re some kind of magic shield. Flip on CONFIG_RANDOMIZE_BASE=y for KASLR, tick the box, and suddenly the system’s “hardened.” Turn on SMEP and SMAP in the BIOS, and security closes out the ticket. Job done, right?
But if I stopped you and asked, “Which actual attack techniques did you just block? Which ones still work exactly as before?”—could you answer?
The Problem: Security Theater vs. Real Engineering
Most teams think these switches are all-or-nothing. Secure or not. That’s a fantasy. The truth is, it’s all about nuance. If you’re enabling features without really understanding how the CPU and memory work under the hood, you’re just putting on a show.
The real question isn’t “Is this on?” It’s “How much harder did we just make it to pull off a real VM escape?” This is the core philosophy of our Virtualization Architecture Pillar: security must be measurable, not just compliant.
Threat Model: What Are We Really Up Against?
Let’s cut through the buzzwords. We’re not fighting off generic “hackers.” We’re up against specific memory corruption attacks that lead to Ring 0 code execution.
In a hypervisor context, here’s what actually matters:
- Post-Exploitation Escalation: An attacker already inside a guest VM or a user process wants to go all the way up to kernel level and stick around.
- VM Escape: This is the big one. Chaining together bugs to break out of the VM and run code in the hypervisor’s kernel.
- ROP/JOP Chains: Using little pieces of the kernel’s own code—gadgets—to create new behaviors because injecting your own code isn’t an option.
- Ret2usr: Tricking the kernel into running code sitting in user memory, but with Ring 0 privileges.
If you don’t know how these attacks work, you can’t build real defenses. You’re just guessing.
Control Breakdown: Looking Through the Attacker’s Eyes
To know if these controls matter, you have to think like someone writing exploits. It’s not about what the feature claims to do—it’s about what techniques it actually breaks.
KASLR (Kernel Address Space Layout Randomization)
- What it Breaks: Static ROP and JOP chains. If an attacker hardcodes memory addresses to find a kernel function (like
commit_creds), KASLR shuffles everything around on every boot. - What it Doesn’t Break: Info leaks. If a bug lets an attacker see just one kernel pointer, they can figure out the whole layout. At that point, KASLR is basically useless.
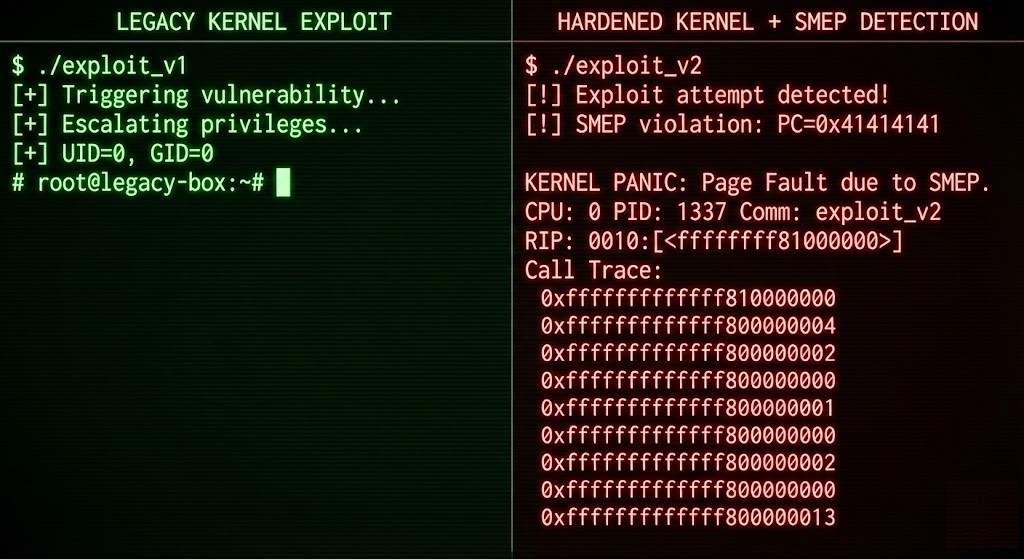
SMEP (Supervisor Mode Execution Prevention)
- What it Breaks: Ret2usr. Attackers used to load a payload in user memory and trick the kernel into jumping there. SMEP flips a CPU bit so the kernel will crash if it tries to execute from user memory.
- What it Doesn’t Break: Code reuse attacks. As long as the attacker sticks to chaining together existing kernel code, SMEP can’t stop them.
SMAP (Supervisor Mode Access Prevention)
- What it Breaks: Arbitrary kernel read/writes to user memory. It stops the kernel from touching user-space data, unless it’s been given explicit permission. This blocks exploits that rely on the kernel picking up fake data from user memory.
- What it Doesn’t Break: Attacks that only mess with kernel memory. If everything the attacker wants to corrupt is already inside the kernel, SMAP can’t help.
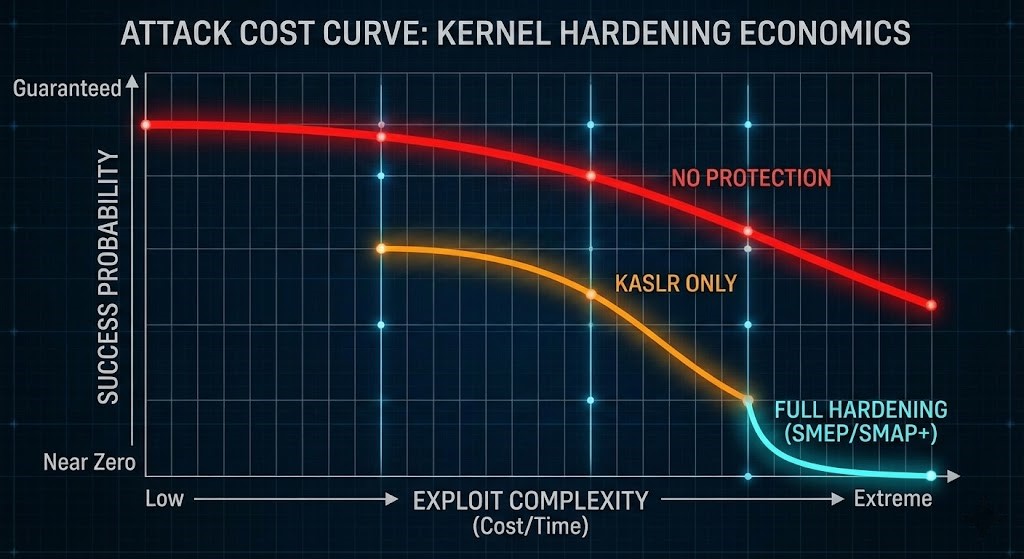
Measuring Attack Surface Reduction (The Actual Benefit)
This is where things get real. Let’s ditch the generalities and talk about engineering. How much do these switches really raise the bar for an attacker?
Here’s the breakdown:
| Dimension | Without Controls | With KASLR | With SMEP | With SMAP | With ALL |
| Static ROP Viability | High | Low | Low | Low | Near-Zero |
| Ret2usr Viability | High | High | Near-Zero | Near-Zero | Near-Zero |
| Arbitrary Kernel R/W | High | Medium | Medium | Low | Low |
| VM Escape Reliability | High | Medium | Medium | Low | Very Low |
| Exploit Chain Length | Short (1-step) | Medium (Needs Leak) | Long (ROP only) | Very Long | Extreme |
With All Controls: Everything is tougher. Now, to pull off an exploit, an attacker needs an info leak (to beat KASLR), a write primitive (to set up the chain), and a full ROP chain (to get around SMEP and SMAP). What used to take a day now takes months of research.
Failure Modes: Where the Defenses Crack
Let’s be straight about this—these controls aren’t magic.
- Info Leaks: If an attacker gets even a single kernel pointer, KASLR is dead. The randomization is gone.
- JIT Spraying: Some advanced attacks (think JIT spraying in browsers, or eBPF tricks in kernels) can still generate code that sidesteps SMEP/SMAP.
- Third-Party Drivers: The hypervisor kernel might be locked down, but that off-the-shelf RAID controller driver? It might open up dangerous IOCTL paths that blow right past all your hardening.
The Verdict: Respect the Engineering
These controls raise the bar, but they don’t make you invincible. If you’re not paying attention to the details, you’re just playing security dress-up.
By enabling and verifying KASLR, SMEP, and SMAP, you aren’t making your hypervisor “unhackable.” You are pricing the average attacker out of your environment. In 2026, security isn’t about stopping the attack; it’s about making the attack too expensive to be worth the effort.
“Kernel hardening doesn’t stop attackers — it prices them out of your environment.”
Next Steps:
- Audit: Use the techniques above to verify your current KASLR/SMEP status.
- Learn: Follow the Virtualization Security Learning Path to master advanced hypervisor hardening.
- Architect: Review the Virtualization Architecture Pillar for broader design principles.
Additional Resources
- Intel SDM Vol. 3 – Supervisor Mode Execution Prevention (SMEP): The definitive hardware specification for CR4 register controls.
- Linux Kernel Documentation – KASLR: Technical details on how the Linux kernel implements address randomization.
- MITRE CVE-2023-XXXX Case Studies: Review recent kernel privilege escalation CVEs to see how many require “chaining” to bypass SMEP/SMAP.
- Project Zero – Exploiting the Linux Kernel: Advanced reading on how researchers bypass modern kernel mitigations.
Editorial Integrity & Security Protocol
This technical deep-dive adheres to the Rack2Cloud Deterministic Integrity Standard. All benchmarks and security audits are derived from zero-trust validation protocols within our isolated lab environments. No vendor influence.
This architectural deep-dive contains affiliate links to hardware and software tools validated in our lab. If you make a purchase through these links, we may earn a commission at no additional cost to you. This support allows us to maintain our independent testing environment and continue producing ad-free strategic research. See our Full Policy.