Rubrik vs. Veeam in the Sovereign Estate: Choosing the Right Guard for Your Data
In commercial IT, backup is a game of performance metrics – restore speeds, compression ratios, and storage efficiency.
In a Sovereign Estate – AWS GovCloud, Azure Government, or an isolated on-premise enclave – backup becomes something else entirely: Jurisdictional Risk Control.
You are no longer protecting data from disk failure; you are protecting authority from compromise. In these environments, the internet may not exist, identity providers may fail, and vendors strictly cannot “phone home.”
This means your backup system is no longer a utility. It is the last surviving control plane. This is why backup architecture sits at the very center of the Data Protection Architecture Pillar.
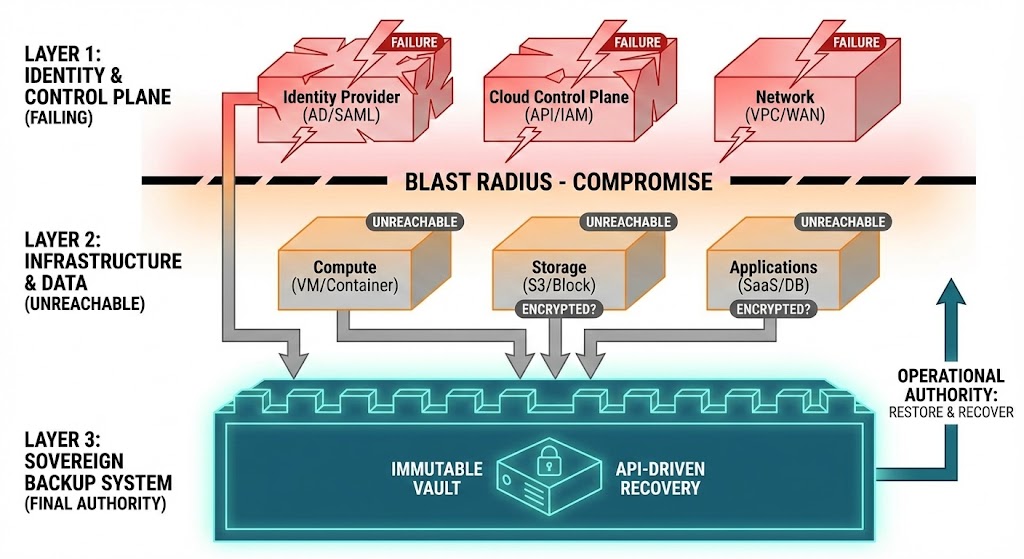
The Sovereign Constraint: Surviving Total Failure
A sovereign system is defined not by its features, but by its ability to survive three specific failure modes:
- Identity Outage: No one can authenticate via standard SSO.
- Control Plane Outage: Cloud APIs become unreachable.
- Legal Isolation: Data cannot be exported or accessed by foreign support staff.
This aligns directly with the modern resilience modeling discussed in our Cloud Strategy Pillar.
The real decision between Veeam and Rubrik is not “Which backs up faster?” It is: Where does operational authority live when everything else fails?
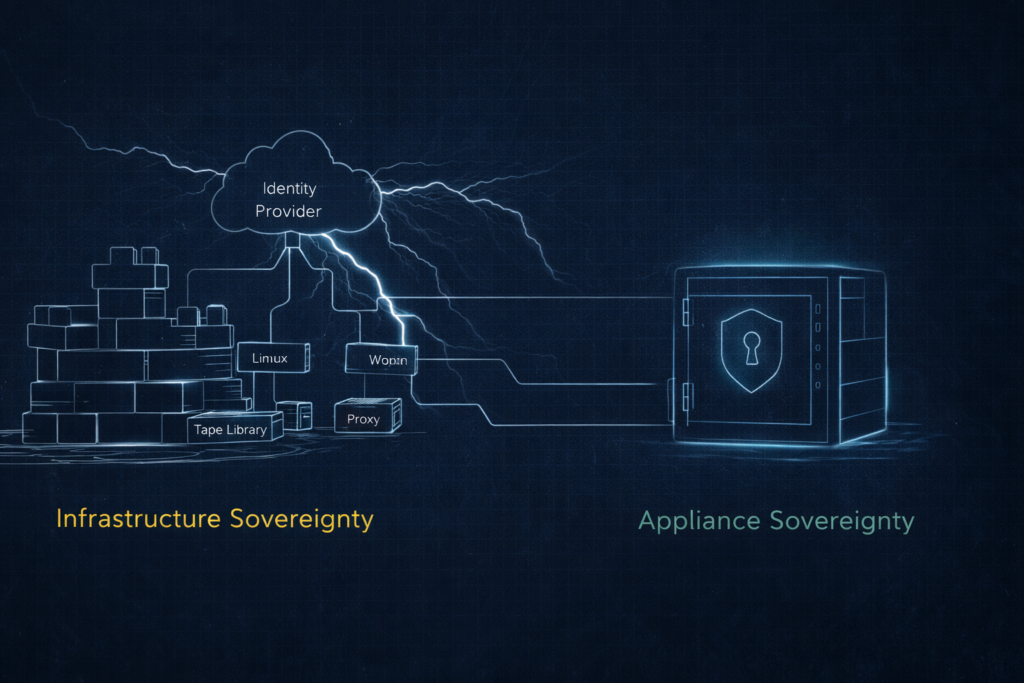
The Architectural Split
Veeam — Infrastructure Sovereignty
Veeam is not a product; it is a framework you assemble. You build the Backup Server, the Proxy Servers, the Hardened Repositories, and the Tape Infrastructure. You own every layer.
- The Sovereign Advantage: You control the blast radius. There are no opaque services, hidden dependencies, or vendor-managed operating systems.
- The Tradeoff: You inherit the responsibility for patching, credential hardening, and lateral movement protection. In sovereign estates, this complexity matches the philosophy of the Modern Infrastructure & IaC Strategy Guide, but it also means the infrastructure itself becomes an attack surface.
Rubrik — Appliance Sovereignty
Rubrik flips the model. You do not manage backup infrastructure; you define policies. The system enforces immutability through its internal filesystem architecture.
- The Sovereign Advantage: The backup environment becomes non-mountable, API-mediated, and logically air-gapped. Ransomware cannot encrypt what it cannot reach.
- The Tradeoff: Authority shifts from infrastructure control to trust in the appliance design. You cannot inspect every layer. For some operators, this reduces risk; for others, it violates the audit philosophy. This aligns with the resiliency concepts taught in the Data Protection Resiliency Learning Path.
The Air-Gap Reality: Physical vs. Logical
In sovereign estates, the “Air-Gap” is where the architectural decision is often made for you.
Physical Air-Gap (Veeam’s Domain)
Required in certain regulatory environments (Top Secret/SCI), this involves tape vaulting, offline rotation, and manual custody chains.
- Why Veeam Wins Here: It dominates because it integrates deeply with legacy ecosystems and tape libraries. The architecture assumes humans will move the media.
Logical Air-Gap (Rubrik’s Domain)
Modern sovereign estates increasingly rely on logical isolation: immutable snapshots, role separation, and cryptographic lockout.
- Why Rubrik Wins Here: It excels because the architecture assumes software enforces the separation.
Control Plane Survivability
The true test of backup is simple: Can you recover when identity is compromised?
In a real incident, Active Directory is likely compromised, Cloud IAM is unreachable, and Monitoring is offline. Your backup platform becomes the last authority. This is the exact failure model explored in our analysis of Deterministic Tools for a Non-Deterministic Cloud.
Operational Gravity — The Real Decision
You are not choosing a vendor. You are choosing where failure is allowed to exist.
| Factor | Veeam (Infrastructure) | Rubrik (Appliance) |
| Authority Location | Infrastructure | Appliance |
| Attack Surface | Larger (OS/Network) | Smaller (API/Blackbox) |
| Audit Transparency | Maximum | Abstracted |
| Operational Burden | High | Moderate |
| Legacy Compatibility | Excellent | Limited |
| Ransomware Resistance | Configured | Native |
The Rack2Cloud Verdict
Choose Veeam When:
- You operate a heterogeneous sovereign estate with legacy operating systems or tape mandates.
- You have strict audit inspection requirements that demand full visibility into the OS.
- You have a dedicated security engineering staff available to harden the stack.
- You want sovereignty to live in process and infrastructure.
Choose Rubrik When:
- You operate a modern virtualized or cloud-aligned estate.
- Ransomware is your primary threat model.
- Staffing is limited, and recovery speed is prioritized over infrastructure control.
- You want sovereignty to live in architecture and immutability.
Rack2Cloud Closing Insight
Backup is not storage. Backup is authority.
Authority must survive the failure of identity, cloud control planes, networks, and humans. This is why data protection sits downstream of every other architectural decision—including Virtualization Architecture.
In sovereign estates, you are not selecting a recovery tool. You are selecting the final governing system of your infrastructure. The right choice is the one whose failure mode you trust more.
Additional Resources
The following resources provide industry background, threat intelligence, and architectural context supporting the concepts discussed in this article.
Identity, Authentication & Control Plane Risk
- Cybersecurity and Infrastructure Security Agency — Guidance on identity infrastructure attacks & resilience strategies
- National Institute of Standards and Technology — Zero Trust Architecture (SP 800-207)
- Microsoft Security Response Center — Real-world identity provider compromise case studies
- Google Cloud Security Blog — IAM compromise and control-plane threat analysis
Ransomware, Backup & Recovery Reality
- Mandiant M-Trends Report — attacker dwell time & backup targeting patterns
- Veeam Ransomware Trends Report — attackers targeting backup infrastructure
- Sophos State of Ransomware — recovery vs payment statistics
- IBM Security X-Force Cost of a Data Breach Report
Immutability, Object Lock & Data Authority
- Amazon Web Services S3 Object Lock & WORM storage documentation
- Cloudflare Backup isolation & blast-radius reduction concepts
- ENISA Data resilience & backup isolation recommendations
Editorial Integrity & Security Protocol
This technical deep-dive adheres to the Rack2Cloud Deterministic Integrity Standard. All benchmarks and security audits are derived from zero-trust validation protocols within our isolated lab environments. No vendor influence.
This architectural deep-dive contains affiliate links to hardware and software tools validated in our lab. If you make a purchase through these links, we may earn a commission at no additional cost to you. This support allows us to maintain our independent testing environment and continue producing ad-free strategic research. See our Full Policy.