Sovereign Cloud vs. Public Cloud: Navigating Compliance in a Non-Deterministic Landscape
The Feature Toggle That Broke Compliance
It usually starts with a minor configuration change.
A generic enterprise architecture team hosting EU customer data in a Frankfurt region. They pass the audit. They have the residency certificate. Then, a DevOps lead enables a “Predictive Auto-Scaling” feature on the PaaS layer.
NO breaches., NO bulk exports, and NO database dumps.
But you have just created a new legal access path that falls outside your declared jurisdictional boundary.
The “predictive” element of that scaling feature relies on a global control plane. The moment it activates, system state metadata streams to a central inference engine—often in Virginia—to calculate scale-out triggers.
Engineers often dismiss this as “just logs.” It isn’t.
- Session counts reveal active user geography.
- Error telemetry contains user identifiers (UIDs).
- Memory pressure snapshots can include fragments of regulated payloads because object caches and heap inspection expose application memory pages, not logical records.
Auditors don’t call this a hack; they call it an uncontrolled transfer vector. And it happens the moment you prioritize “smart” features over architectural isolation.
The Myth of Static Residency
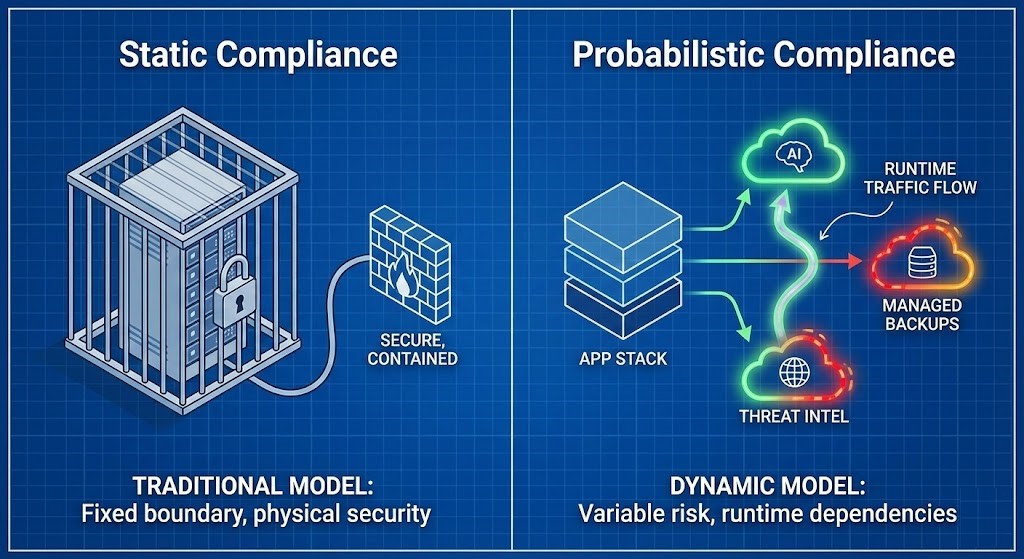
We are working with a broken mental model. Most of us (and I include myself in this from the early virtualization days) were trained to view compliance as a binary state based on physical location.
That model assumes Data Residency (where the disk spins) equals Data Sovereignty (who owns the law).
The Regulatory Reality
We need to be specific about why the old model fails. It’s not just paranoia; it’s codified in law:
- US CLOUD Act: This doesn’t regulate where data sits; it regulates who has “possession, custody, or control” of the system. If a US-based entity has administrative control, the data may be considered within the legal reach of US authorities.
- Schrems II (CJEU): Invalidated the Privacy Shield because US surveillance laws (FISA 702) conflict with GDPR.
- GDPR Processor Obligations: You are responsible for the entire supply chain of sub-processors, including the vendor’s support team.
These regulations don’t regulate disks. They regulate who can be compelled to access systems.
The Non-Deterministic Cloud
This is the pillar concept you need to understand: A non-deterministic cloud is a platform where the legal jurisdiction of data depends on runtime operations rather than storage location.
| System Type | Compliance State |
| Traditional DC | Determined at Deploy Time (Static) |
| Modern Public Cloud | Determined at Runtime (Dynamic) |
| AI-Integrated Cloud | Determined Per Request (Probabilistic) |
The Hidden Flows
Here is where the architecture breaks. These are the mechanics that your account rep won’t mention during the QBR:
| Mechanism | The Engineering Reality |
| Operational Telemetry | Logs are rarely scrubbed at source. They flow to global data lakes for aggregation. |
| WAF Anomaly Detection | To detect Zero Days, your traffic patterns are compared against a global cross-tenant baseline. |
| Support Debugging | “Follow the Sun” support means a crash dump (heap introspection) can be viewed by an engineer in a non-compliant geo. |
| Autoscaling | Policy engines often sit in the global control plane, ingesting metrics from all regions. |
Architecting for True Sovereignty
Treat sovereign cloud claims as an architectural property, not a marketing feature. Most of it is just “Public Cloud with a local flag.”
Sovereign cloud does not make you compliant—it makes compliance provable.
Compliance failure is usually not about illegal storage—it is about unverifiable access authority. You need an architecture that moves from “Trust but Verify” to “Verify then Trust.”
The Catalyst: Why This Matters Now
Why is this hitting us in 2026? Three factors:
- AI Telemetry: Models eat metadata. Your operational exhaust is now valuable training data. Even if your payload data never leaves the region, behavioral signals often do. Rate limits, anomaly scores, bot fingerprints, and usage heuristics are frequently aggregated across regions to improve model accuracy. The payload stays local. The intelligence layer does not. Modern platforms optimize globally, not jurisdictionally—and optimization always wins unless constrained by design.
- Managed Services Dominance: We stopped building servers and started consuming APIs. You don’t own the API gateway; the vendor does.
- Remote Operations: The admin isn’t in the datacenter anymore. They are on a VPN, potentially in a jurisdiction that compels them to hand over keys.
The New Pattern: Jurisdiction-Aware Architecture (JAA)
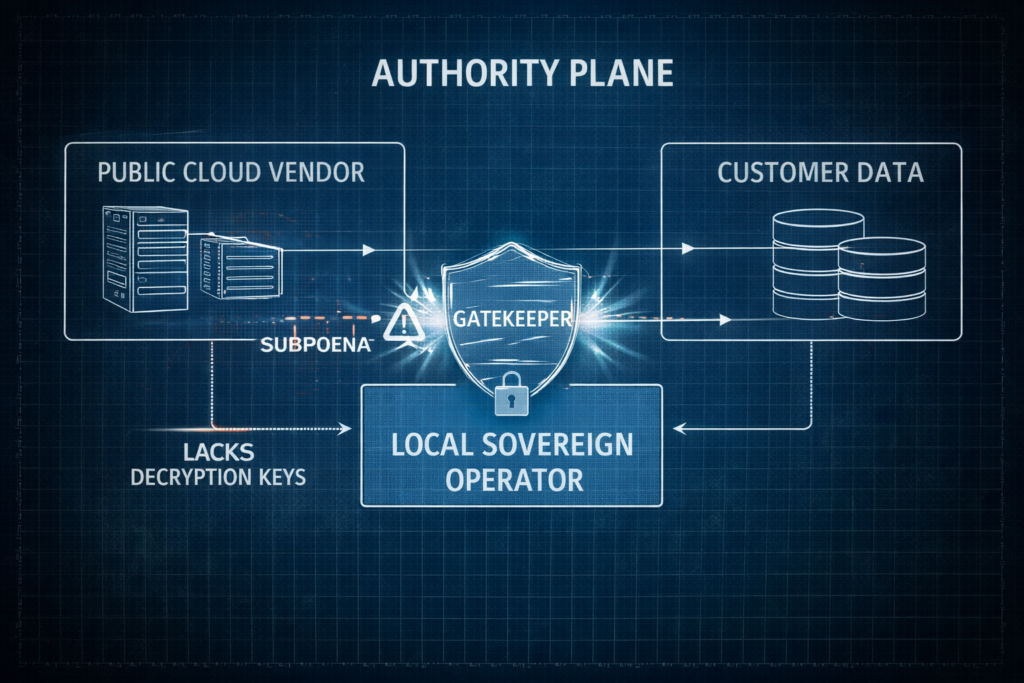
We need to stop designing for “Availability Zones” and start designing for “Legal Execution Paths.” This requires a Jurisdiction-Aware Architecture (JAA).
The core of JAA is the Authority Plane. This plane defines which legal jurisdiction can force operational actions on the platform—including access, inspection, or key usage.
JAA Implementation Matrix
| Control | Example Implementation |
| Authority Isolation | A separate operating company (local entity) controls the virtualization layer. |
| Cryptographic Sovereignty | External HSM quorum approval. The vendor asks for a key; your HSM grants it (or denies it). |
| Deterministic Support | Region-locked support queues. No “Follow the Sun” routing for Sev1s. |
| Observability Filtering | Local log aggregation tier that strips PII/UIDs before shipping metrics to the vendor. |
True sovereignty is not a region selection; it is an operational separation of authority, personnel, and cryptographic control. Without those three, you have regional hosting—not jurisdictional isolation.
For deep dives on implementing these controls, see our Cloud Strategy Pillar and Sovereign Architecture Learning Paths.
The Engineering Verdict
Let’s be real. You aren’t moving everything to a Sovereign Cloud. The latency on the control plane is annoying, the feature lag is real, and the cost is high.
But for your regulated core, the “Shared Responsibility Model” is dead. You cannot treat shared responsibility as symmetrical when legal compulsion is asymmetrical.
You need to shift your thinking: You have regional hosting, not jurisdictional isolation.
The Compliance Design Checklist
Before you sign off on the architecture, ask these specific engineering questions:
- Memory Snapshots: Can vendor support access memory dumps (heap inspection) during a Sev1 without my cryptographic approval?
- Metadata Export: Does the monitoring agent export headers, session IDs, or UIDs to a global lake?
- Key Custody: Are backups encrypted with tenant-managed keys that exist outside the provider’s KMS?
- Control-Plane Execution: Can the provider run diagnostic commands (e.g.,
kubectl exec) inside my tenant without an audit trail I control? - AI/ML Processing: Are any service features (auto-tuning, anomaly detection) using centralized model training pipelines with my operational data?
- Subpoena Pathing: Can a legal order served to the provider’s parent company compel operational action inside my regional tenant?
If the answer to any of these is “It depends,” your compliance posture is not architectural—it is situational.
Editorial Integrity & Security Protocol
This technical deep-dive adheres to the Rack2Cloud Deterministic Integrity Standard. All benchmarks and security audits are derived from zero-trust validation protocols within our isolated lab environments. No vendor influence.
This architectural deep-dive contains affiliate links to hardware and software tools validated in our lab. If you make a purchase through these links, we may earn a commission at no additional cost to you. This support allows us to maintain our independent testing environment and continue producing ad-free strategic research. See our Full Policy.