The 3-2-1-1-0 Rule: Modernizing Backup Protocols for 2026 Cyber-Resilience
The traditional 3-2-1 backup strategy was designed to solve for hardware failure; the 3-2-1-1-0 rule is engineered to solve for adversarial intent. In a landscape where 94% of ransomware attacks now specifically target the backup server, a “copy” is no longer a recovery asset unless it is cryptographically or physically isolated from the production plane.
The Mechanics of the “1-0” Extension
The leap from “Standard Backup” to “Cyber Resilience” happens in the final two digits of the protocol. This framework is a core component of our Cloud Learning Path, where we move from legacy redundancy to modern deterministic recovery.
- 3 (Copies of Data): Maintain three distinct instances of data—the primary production data and two backup copies.
- 2 (Different Media Types): Store copies on at least two disparate storage technologies. For hybrid architects, this often means splitting data between local NVMe and S3-compatible object storage.
- 1 (Off-site Copy): Geographically separate at least one copy to safeguard against localized physical disasters.
- 1 (Immutable or Air-Gapped): This is your Last Line of Defense. Modern immutability is enforced through S3 Object Lock or WORM (Write Once, Read Many) protocols that prevent deletion, even if admin credentials are compromised.
- 0 (Zero Errors / Verified Recovery): This represents Recovery Assurance. Verification must move from simple success logs to automated, script-based testing where VMs are booted in an isolated sandbox.
WORM (Write Once, Read Many): A data storage technology that allows data to be written to a storage medium once and prevents the data from being erased or modified. Air-Gap: A security measure that ensures a secure computer network is physically isolated from unsecured networks, such as the public internet or an unsecured local area network.
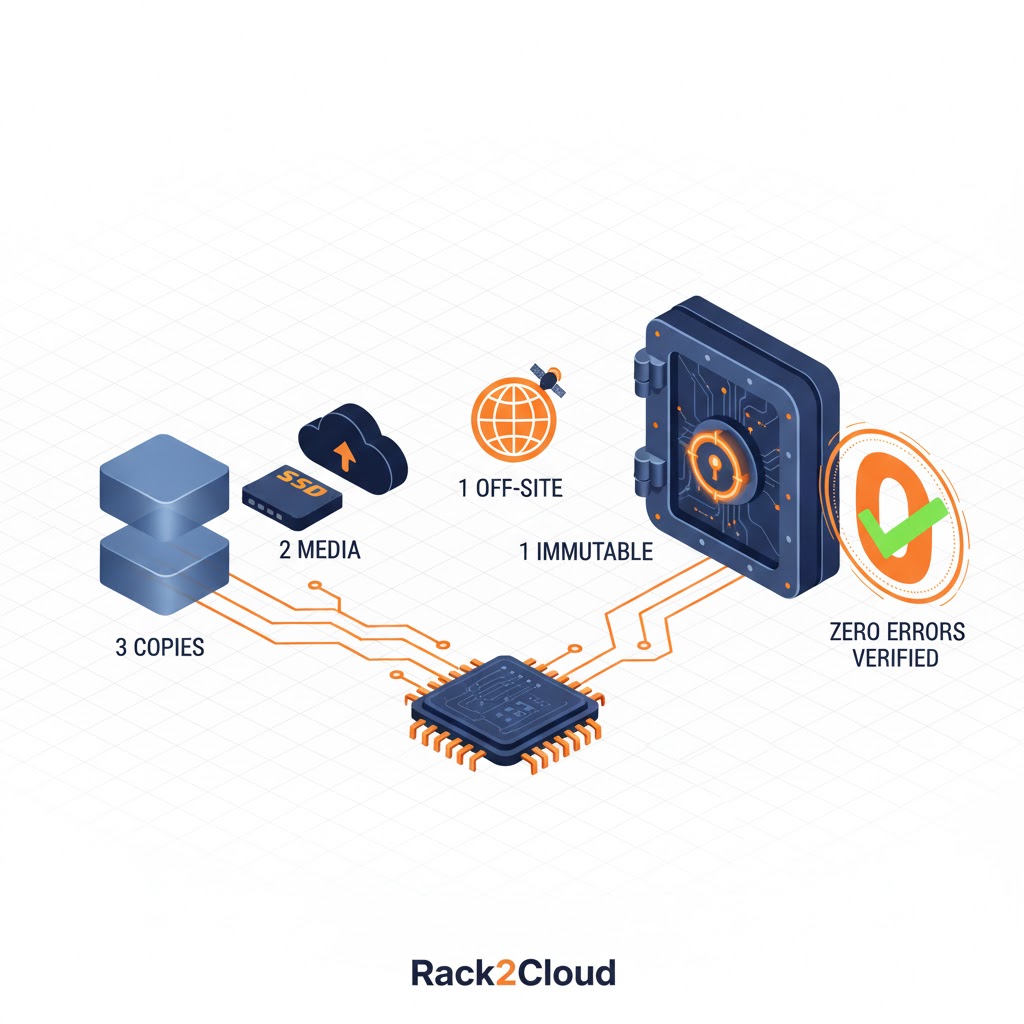
Image 1: 3-2-1-1-0 Backup Rule
Deep Dive: Competitive Immutability Architecture
Architects must distinguish between software-defined locks and hardened, immutable file systems.
| Platform | Mechanical Implementation of the “1” | 2026 Technical Distinction |
| Nutanix Objects | S3 Object Lock (Compliance Mode) | Native to AOS; leverages WORM buckets to prevent deletion even by a Cluster Admin. |
| Veeam Hardened Repo | Linux XFS Immutability | Uses the i attribute at the file system level to prevent modification of VIB/VBK files. |
| Cohesity | SpanFS + Helios | A distributed file system that uses a strict read-only snapshot architecture with DataLock. |
| Rubrik | Atlas File System | Custom, purpose-built file system that is “immutable by design.” |
Nutanix Objects: Native S3 Compliance
For organizations following our Nutanix AHV Architectural Guide, Nutanix Objects provides a deterministic path to 3-2-1-1-0 by utilizing native S3 Object Lock in Compliance Mode. Even if a bad actor gains access to the Nutanix Prism console, the underlying storage blocks cannot be reclaimed or overwritten until the retention timer expires.
Veeam: The Linux Hardened Repository (LHR)
Veeam addresses the “1” by leveraging the immutability flag within the Linux XFS file system. It uses the chattr +i attribute to lock backup files locally, utilizing non-root users and limited permissions. For the “0” factor, Veeam SureBackup remains an industry standard, automating heartbeat and application tests in a Virtual Lab.

Platform-Specific Fiscal Logic (1PB TCO)
Managing the costs of these resilience tiers requires specialized utilities. You can model these requirements using our Deterministic Architecture Tools.
- Nutanix Objects (The Sunk Cost Advantage): For shops already running AOS, the TCO for immutability is significantly lower as physical infrastructure is already accounted for. You avoid the “Infrastructure Silo Tax” of buying separate hardware.
- Veeam (The Flexibility Model): Veeam allows you to build a high-performance 3-2-1-1-0 stack using commodity hardware, lowering upfront CapEx. This is a common entry point in our Virtualization Learning Path.
- Rubrik (Premium Peace of Mind): While acquisition costs are higher, TCO shines in labor reduction. Automated malware scanning can reduce the need for a dedicated Backup Administrator by up to 50% and may lower cyber insurance premiums.
- Cohesity (Data Consolidation): SpanFS allows you to use one platform for both 3-2-1-1-0 backups and production NAS, splitting hardware costs across departments.
Strategic Recommendation: The “Sweet Spot”
- Under 250TB (Nutanix Shop): Stick with Nutanix Objects. The lack of a new “silo” provides the best TCO and operational consistency.
- 250TB – 1PB (Heterogeneous): Veeam is the architectural winner. It allows you to build a high-performance stack using your choice of server hardware.
- Over 1PB / Zero-Trust Focus: Move to Rubrik or Cohesity. At this scale, the global deduplication and AI-driven “0 Error” verification provide a better ROI as recovery complexity outpaces human management capacity.
Additional Resources:
Editorial Integrity & Security Protocol
This technical deep-dive adheres to the Rack2Cloud Deterministic Integrity Standard. All benchmarks and security audits are derived from zero-trust validation protocols within our isolated lab environments. No vendor influence.
Get the Playbooks Vendors Won’t Publish
Field-tested blueprints for migration, HCI, sovereign infrastructure, and AI architecture. Real failure-mode analysis. No marketing filler. Delivered weekly.
Select your infrastructure paths. Receive field-tested blueprints direct to your inbox.
- > Virtualization & Migration Physics
- > Cloud Strategy & Egress Math
- > Data Protection & RTO Reality
- > AI Infrastructure & GPU Fabric
Zero spam. Includes The Dispatch weekly drop.
Need Architectural Guidance?
Unbiased infrastructure audit for your migration, cloud strategy, or HCI transition.
>_ Request Triage Session





