Azure Governance Needs More Unix: The “BSD Jail” Pattern for Landing Zones
This strategic advisory has passed the Rack2Cloud 3-Stage Vetting Process: Market-Analyzed, TCO-Modeled, and Contract-Anchored. No vendor marketing influence. See our Editorial Guidelines.
Stop “archi-splaining” governance to your engineers.
Modern cloud governance has mutated into a bloated bureaucratic layer that tries to micro-manage every resource through 400-page PDF frameworks. Somewhere along the way, we forgot the lesson Unix taught us forty years ago: Freedom within boundaries.
A recent fintech client of ours had 14 subscriptions, nearly 400 Azure Policy definitions, and a governance board that met weekly to approve exceptions. Despite all that “control,” they suffered three lateral movement incidents in a single quarter — simply because no one could clearly answer one question:
Who actually owns what?
This wasn’t a tooling failure. It was a governance failure.
We need to stop treating Azure subscriptions like billing buckets and start treating them like BSD Jails.
Key Takeaways
- Stop Archi-splaining: Developers don’t need a compliance framework — they need a
chrootenvironment. - Design for Blast Radius, Not Compliance Score: A high Secure Score means nothing if one identity can traverse your entire tenant.
- Governance Must Accelerate Delivery: If your security model slows production, it is a failed model.
- The Subscription IS the Jail: Treat the subscription boundary as a hard kernel limit.
The Failure of the “Nanny Cloud”
The standard “Enterprise Scale” model — where Central IT approves every NSG rule, route table, and resource creation — is fundamentally broken. It tries to solve technical problems with human processes.
That centralization creates three predictable failure modes:
- Approval Bottlenecks: Change velocity collapses as tickets pile up in the “Cloud Approval” queue.
- Permission Drift: Emergency exceptions get granted to bypass the bottleneck — and then never revoked.
- Shadow Infrastructure: Frustrated teams spin up “Pay-As-You-Go” subscriptions outside the platform just to get work done.
Each of these increases either your breach probability or your mean time to recovery — often both. This is how you end up with the worst of all worlds: slow delivery, weak security, and zero accountability.
The Architecture — Subscription as a “BSD Jail”
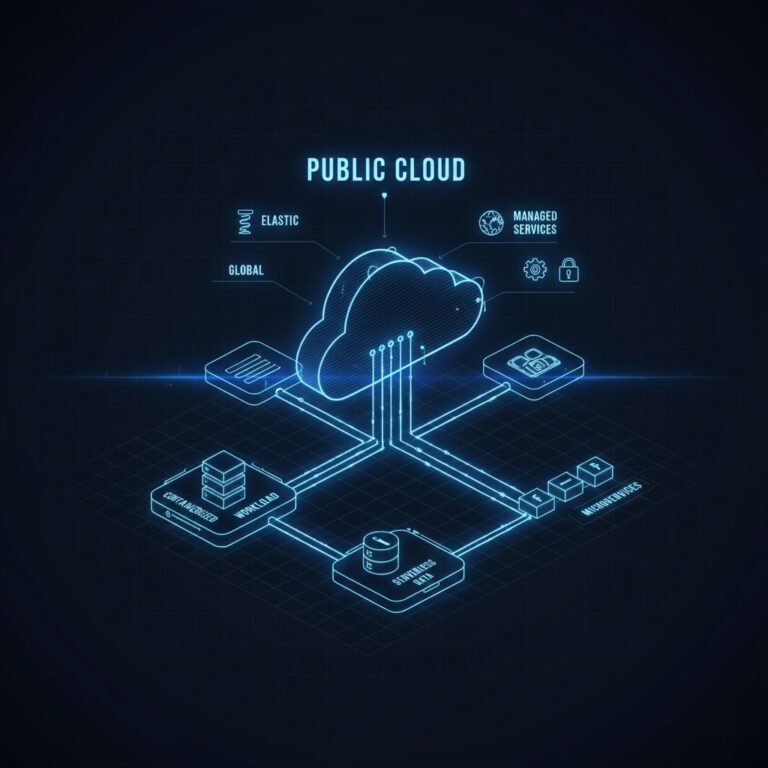
In Unix, a BSD Jail limits the scope of root. Unlike a simple chroot, it isolates users, processes, and networking. You can destroy your own environment — but you can’t touch the kernel or other jails.
In Azure, we must apply the same logic. The Subscription is the Jail.
- Kernel Space (Hub): Managed by Platform Engineering. Contains the firewall, identity infrastructure, ExpressRoute, DNS, and routing controls. Immutable to workload teams.
- User Space (Spoke): Managed by the workload team. They have freedom within boundaries to deploy what they need — as long as they cannot route out of their jail or modify the kernel.
The Explicit Threat Model This pattern is explicitly designed to prevent:
- Lateral Movement: An identity compromised in Spoke A has zero permissions in Spoke B.
- Privilege Escalation: Even Contributors cannot modify peering, UDRs, or control-plane routes.
- Subscription Breakout: Hard quotas and deny policies prevent accidental blast radius expansion.
The goal isn’t to prevent mistakes. The goal is to make mistakes survivable.
Case Study: The CI/CD Wipe A SaaS provider using standard CAF Enterprise Scale suffered a breach when a compromised CI/CD identity escalated to Subscription Owner and wiped three environments.
Under the BSD Jail Pattern, that identity would have been trapped inside a single Resource Group — turning a catastrophic business event into a minor incident ticket. Recovery would have taken minutes, not weeks.
The “Dark Art” of RBAC Delegation
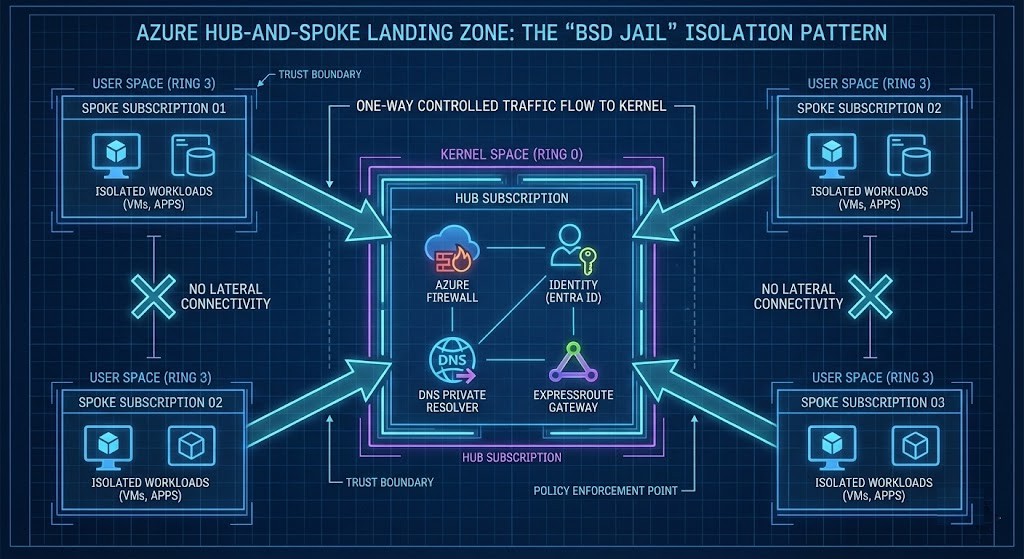
Most Landing Zones fail because Azure RBAC forces a false binary:
- Reader — useless.
- Contributor — dangerous.
The fix is constrained delegation. Azure RBAC was designed for centralized IT, not decentralized engineering teams — which is why most organizations misuse it.
Three Delegation Patterns That Actually Work
- The Project Lead Model: Can manage Resource Groups and assign contributors downstream — but cannot assign
Owneror modify subscription-level roles. - The Platform Operator Model: Can manage compute and networking inside the subscription — but cannot modify Hub peering, DNS, or routing controls.
- The Security Observer Model: Read-only access plus security insights (Defender, Sentinel) — with zero write permissions.
RBAC Anti-Patterns to Avoid
- Contributor at Subscription Root: The “lazy admin” button. Grants too much control-plane power.
- Security Team as Owner: Security should audit the platform — not own the keys to the kingdom.
- Everyone gets User Access Administrator: This breaks the chain of custody for identity management.
Security Outcome Matrix
Executives need measurable outcomes — not governance theater.
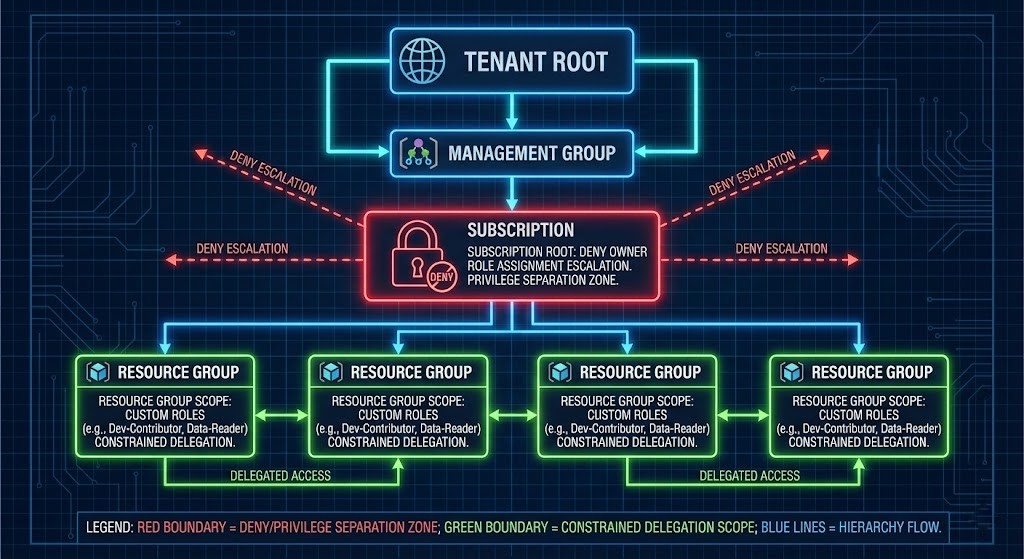
| Governance Model | Blast Radius | Mean Time to Provision | Lateral Movement Risk | Audit Complexity |
| CAF Enterprise Scale | Large (shared dependencies) | High (approval gates) | High (over-privileged identities) | High (policy sprawl) |
| BSD Jail Pattern | Small (isolated units) | Low (pre-approved sandbox) | Low (hard boundaries) | Low (scope provable) |
This is not a tradeoff. It’s a Pareto improvement.
A Migration Path from CAF to Jails
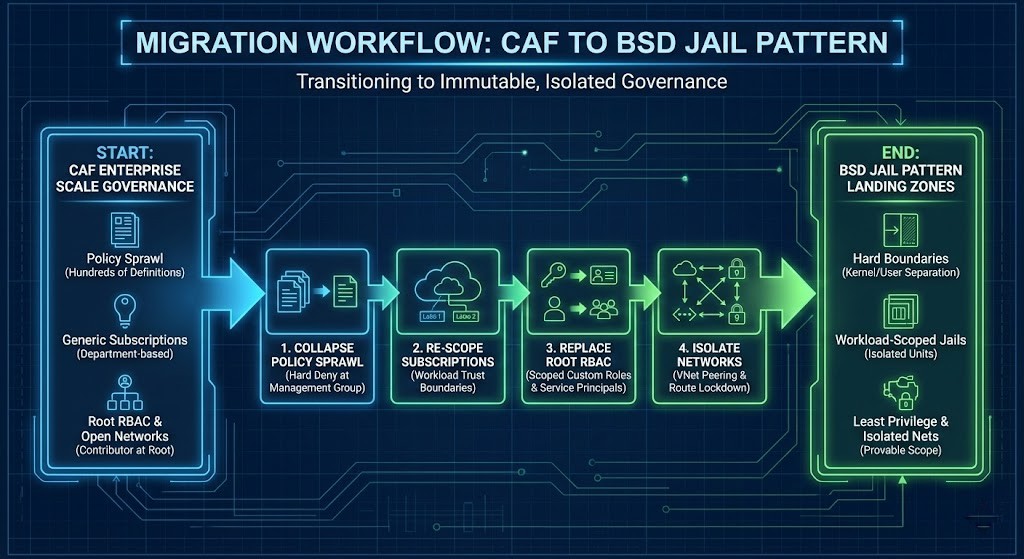
You cannot just flip a switch. Most organizations fail here — not because the model is wrong, but because they try to retrofit governance without refactoring ownership.
Here’s a practical path forward:
- Collapse Policy Sprawl: Replace hundreds of “audit” policies with a few hard deny policies at the Management Group level:
- Deny Public IP creation
- Deny direct peering creation
- Deny unsupported SKUs
- Re-Scope Subscriptions: Move away from “Department” subscriptions (HR, Finance) and toward Workload Trust Boundary subscriptions (Payment Processor, Web Front End).
- Replace Root RBAC: Strip
Contributorfrom the subscription root. Replace it with Modern Infrastructure & IaC service principals and scoped custom roles for workload teams. - Isolate Networks: Enforce kernel/user plane separation by locking down VNet peerings, Route tables, and DNS/firewall paths.
Compliance & the “Click-Ops” Trap
Regulated readers will ask: “Does this work for HIPAA, PCI, or FedRAMP?”
Yes — and it works better.
The Jail model strengthens compliance by making scope provable. Instead of relying on surveillance (logging everything), you rely on segmentation — mathematically proving access is impossible. Auditors don’t need more logs. They need smaller blast radii.
However, you cannot maintain this with Click-Ops. Manual governance creates systemic risk:
- Drift: What’s deployed $\neq$ what’s approved.
- Non-Repeatability: Every jail becomes slightly different.
- Non-Auditability: There is no git commit history for a portal click.
To succeed, you must follow a Modern Infrastructure & IaC Path — stamping out these jails deterministically.
Conclusion
If your governance model requires a weekly steering committee, it is already broken.
Cloud complexity has tricked us into thinking we need complex controls. We don’t. We need simple, hard boundaries. We need to stop writing rulebooks and start building jails.
This isn’t just an Azure concept. Whether you use AWS Accounts with SCPs or GCP Projects with Folders, the physics are the same: Isolation beats policy.
If you want governance that engineers don’t hate and attackers can’t escape — start building jails, not frameworks.
Additional Resources
- The Unix Philosophy (Origin)
- Azure Custom Roles Documentation
- NIST Guide to General Server Security (Segmentation)
This architectural deep-dive contains affiliate links to hardware and software tools validated in our lab. If you make a purchase through these links, we may earn a commission at no additional cost to you. This support allows us to maintain our independent testing environment and continue producing ad-free strategic research. See our Full Policy.