The Public Internet is Not an SLA: Architecting Deterministic Multi-Cloud Interconnects
I once debugged a “random” application timeout for a Chicago-based trading platform. The developers blamed the code; the sysadmins blamed the database. I blamed the weather.
It turned out their critical API traffic was traversing the public internet via a standard IPsec VPN. A fiber cut in Ohio had forced BGP to re-route their traffic through a congested ISP node in Atlanta, adding 45ms of latency. That 45ms was enough to trigger their application’s strict timeout threshold.
They were betting millions of dollars in transaction volume on “Best Effort” routing.
If you are an Enterprise Architect, here is the hard truth: The public internet is not an SLA. You cannot guarantee 99.99% availability if the transport layer is owned by no one and managed by everyone. In 2026, multicloud networking isn’t about connecting VPNs; it’s about building deterministic, private interconnects that ignore the weather.
The Physics: “Best Effort” vs. Deterministic
Why does the internet fail for enterprise workloads? Because of BGP (Border Gateway Protocol). BGP is designed to keep the internet alive, not to keep it fast. If the shortest path is congested, BGP might route your packet around the world just to deliver it.
The Solution: The Private Interconnect Services like AWS Direct Connect (DX) or Azure ExpressRoute are not just “faster cables.” They are dedicated lanes. When you buy a 10Gbps DX circuit, you are buying a guarantee that your packets will not fight with Netflix traffic for bandwidth.
Decision Framework:
- Use Internet/VPN IF: Traffic is non-critical, low-volume (<1TB/mo), and latency insensitive (e.g., nightly backups).
- Use Private Interconnect IF: You need <5ms jitter, >50TB/mo transfer, or strict data sovereignty (traffic must not traverse public nodes).
Architecture Pattern: The “Sovereign Transit”
The old way of connecting AWS to Azure was the “Trombone Effect”: sending traffic from AWS back to your on-prem data center, only to send it right back out to Azure. This doubles your latency and saturates your on-prem firewall.
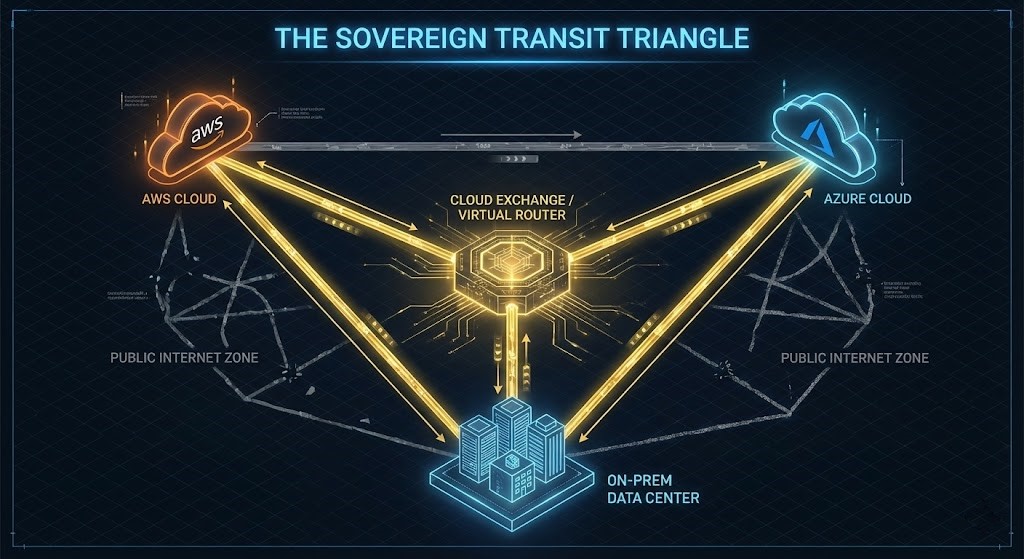
The Modern Standard: Cloud Exchanges Today, we use Cloud Exchanges (like Equinix Fabric or Megaport) to create a “Virtual Router” in the middle.
- AWS VIF connects to the Exchange.
- Azure ExpressRoute connects to the Exchange.
- The Routing: Traffic flows
AWS <-> Exchange <-> Azure.
It never touches the public internet, and it never touches your on-prem hardware. This is the Sovereign Transit pattern.
Critical Tool: When you link these environments, DNS breaks immediately. AWS Route53 cannot resolve Azure Private Zones by default. You will likely create recursive loops trying to fix this. Use the Azure PE Checker to validate your Private Endpoint DNS resolution before you flip the switch.
The Economics: Port Fees as an Arbitrage Strategy
CFOs hate Direct Connect because it has an upfront “Port Fee” (e.g., ~$1000/mo for a 10Gbps port). They prefer VPNs because they are “free.”
They are wrong. They are forgetting the Egress Arbitrage. Hyperscalers charge significantly less for data leaving via a private link than via the internet.
- AWS Data Transfer Out (Internet): ~$0.09 per GB
- AWS Data Transfer Out (Direct Connect): ~$0.02 per GB
The ROI Calculation: If you are moving 100TB a month:
- Internet Egress: $9,000
- Direct Connect Egress: $2,000 + $1,000 (Port Fee) = $3,000
- Savings: $6,000 / month.
Architect’s Action: Stop guessing. Use our Cloud Egress Calculator. Plug in your estimated “Cross-Cloud” traffic. If the savings cover the port fee, the performance upgrade is effectively free.
Failure Domains & The “Active/Active” Myth
The most dangerous network I ever audited had “Redundant” Direct Connects. The client had bought two circuits from the same carrier, terminating in the same AWS location (e.g., Equinix DC1).
When a power distribution unit (PDU) failed in that specific cage, both “redundant” links went dark instantly.
True Diversity Requires:
- Carrier Diversity: One link via Verizon, one via Lumen.
- Physical Diversity: Different conduits entering the building (ask for the “Meet-Me Room” maps).
- Location Diversity: Terminate one link in “Location A” and the backup in “Location B.”
Validation Step: You cannot trust the “Green Checkmark” on the AWS console. You must actively test the latency differences. Use the Metro Latency Monitor to ping across both links simultaneously. If the latency is identical down to the microsecond, they are likely sharing a physical fiber path somewhere.
Conclusion: The Connectivity Maturity Model
Where does your organization sit?
- Level 1 (Amateur): “We use IPsec VPNs over the internet because it’s cheap.” (High Risk, High Latency).
- Level 2 (Pro): “We have a single Direct Connect to our primary region.” (Low Latency, Single Point of Failure).
- Level 3 (Architect): “We use a Cloud Exchange with redundant circuits and BGP multipathing.” (Deterministic, Resilient, ROI Optimized).
Don’t let your million-dollar cloud architecture fail because of a ten-dollar internet connection. Build the blue line.
Additional Resources:
- Hyperscaler Networking Docs: AWS Direct Connect User Guide – Verified pricing and redundancy models.
- Cloud Exchange Specs: Equinix Fabric Documentation – Reference for virtual routing standards.
- BGP Optimization: Cloudflare Learning Center – Context on public internet routing inefficiencies.
Editorial Integrity & Security Protocol
This technical deep-dive adheres to the Rack2Cloud Deterministic Integrity Standard. All benchmarks and security audits are derived from zero-trust validation protocols within our isolated lab environments. No vendor influence.
Get the Playbooks Vendors Won’t Publish
Field-tested blueprints for migration, HCI, sovereign infrastructure, and AI architecture. Real failure-mode analysis. No marketing filler. Delivered weekly.
Select your infrastructure paths. Receive field-tested blueprints direct to your inbox.
- > Virtualization & Migration Physics
- > Cloud Strategy & Egress Math
- > Data Protection & RTO Reality
- > AI Infrastructure & GPU Fabric
Zero spam. Includes The Dispatch weekly drop.
Need Architectural Guidance?
Unbiased infrastructure audit for your migration, cloud strategy, or HCI transition.
>_ Request Triage Session





