The Multi-Hypervisor Future: How Architects Are Designing Beyond VMware
In my fifteen years of architecting enterprise stacks, I’ve seen vendors come and go, but I’ve never seen a shift quite like the one we are witnessing today. For two decades, VMware wasn’t just a hypervisor; it was the bedrock of the data center. You didn’t choose it—you standardized on it because the ecosystem provided a “warm blanket” of stability.
But as we sit in 2026, that blanket is feeling a lot more like a straitjacket. I’m spending more time in the boardroom than the server room lately, and the conversation is no longer about technical IOPS—it’s about financial risk. The economics of single-vendor virtualization have decoupled from reality. If you aren’t architecting for hypervisor diversity today, you aren’t just technical debt—you’re a fiscal liability.

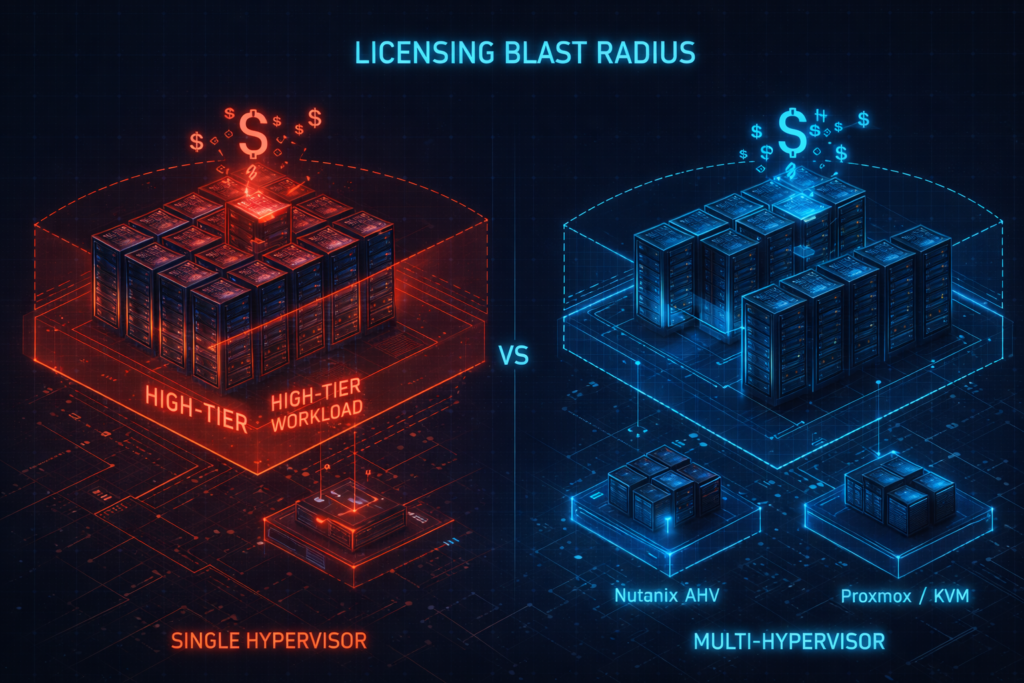
The Licensing Blast Radius: The “Cluster as a Tax Surface” Problem
In the old days, we right-sized by the VM. Today, the modern licensing model treats the cluster, not the workload, as the billing unit. This has created what I call the “Cluster Tax Surface.”
When you have a mission-critical workload that requires a specific high-tier feature (like advanced distributed switching or specific encryption sets), you are often forced to license every single core in that cluster at that premium tier. This means a single domain’s growth can inflate your spend across hundreds of unrelated workloads.
By introducing a multi-hypervisor architecture, you reintroduce cost isolation. You can move workloads with high licensing exposure to platforms like Nutanix AHV or even Proxmox, where their economic profile makes sense—without contaminating the rest of the estate. This isn’t about escaping licensing; it’s about containing the blast radius so one greedy application doesn’t bankrupt your OpEx budget.
Architectural Contenders: Nutanix vs. The Alternate Stack
If you’re looking to offload the VMware tax, you have two primary architectural paths.
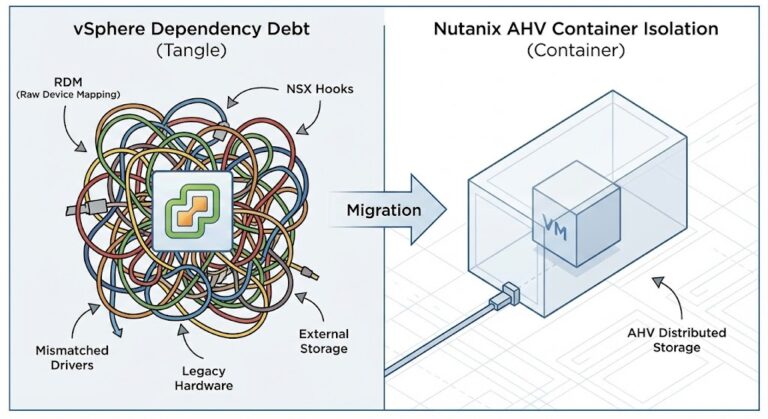
The Nutanix AHV “High-Fidelity” Play
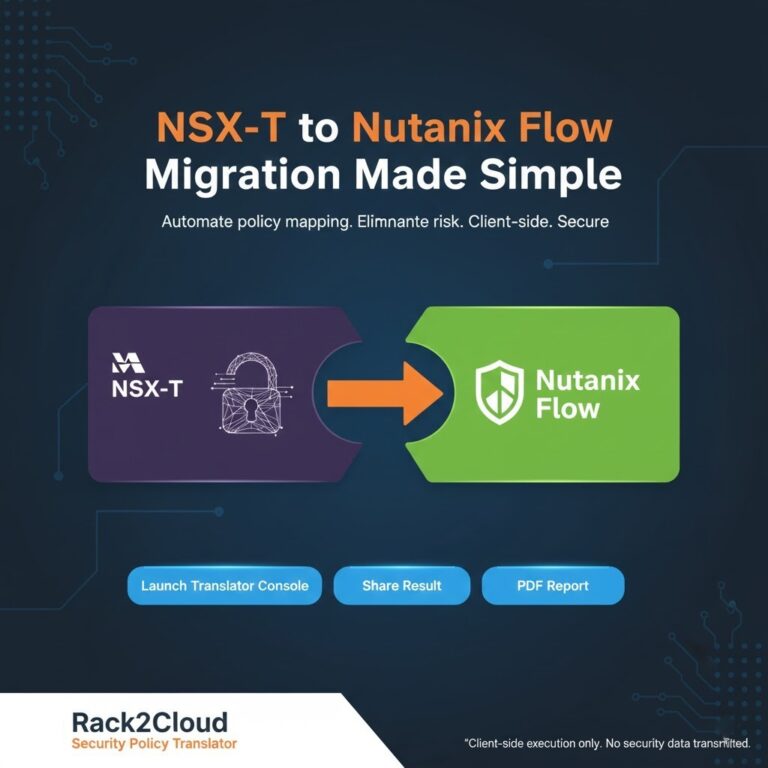
For teams that need to maintain that “Enterprise SDDC” feel, Nutanix is the most logical life raft. It offers the integrated storage and networking (Flow) that architects are used to. If you’re moving from an NSX-T environment, you’ll want to utilize our NSX-T Translator to ensure your security logic doesn’t disappear during the transition.
The Proxmox/KVM “Lean Ops” Play
Proxmox has moved from the “homelab” to the “edge lab” and now to the “enterprise tier.” It’s an incredible tool for Tier-2 workloads and dev environments where you want to sweat your hardware assets without paying a per-core subscription. However, the trade-off is “sweat equity”—you’re trading vendor support for internal engineering prowess. I dive deeper into these trade-offs in our Hypervisor Alternatives Guide.
Decoupling the Control Plane: Design for Mobility
A second hypervisor will either force your automation to mature or cause it to collapse. I’ve seen plenty of shops fail because their Terraform modules were hard-coded to vCenter MoRefs.
Senior architects build platform-agnostic control planes. This means:
- IaC: Using Terraform or OpenTofu modules abstracted by capability, not provider.
- Networking: Visualizing the shift with tools like the V2N Mapper to ensure connectivity remains consistent across stacks.
- Observability: Normalizing logs and metrics via OpenTelemetry so your NOC can’t tell (and doesn’t need to know) which hypervisor a workload is on.
Day-2 Operations: Where the Friction Lives
I always tell my clients: “Migration is a weekend; operations is a decade.” The real risk in multi-hypervisor environments is skill divergence. If your team needs to follow two different runbooks to reset a VM or troubleshoot a network hang, your MTTR (Mean Time to Resolution) will double.
To succeed, you must design for Operational Symmetry. The same monitoring, the same logging taxonomy, and the same incident escalation paths must apply across VMware, Nutanix, and Hyper-V. If your team is struggling to keep up with the shift, check out our resource on Deterministic Tools for a Non-Deterministic Cloud.
The Verdict: Architecture Is Now a Negotiation Strategy
The most compelling observation from my recent consulting engagements is almost paradoxical: the organizations best positioned to leave VMware often choose to stay. Why? Because architectural readiness is pure leverage.
When you walk into a renewal meeting with a validated, tested exit path, the power dynamic shifts. When you’ve used the VMware Core Calculator to expose the hidden core-density costs and ran your environment through the HCI Migration Advisor, you aren’t just speculating—you’re holding a fully costed, technically viable alternative. You are no longer a hostage to a “take it or leave it” subscription model; you have moved from a position of reactive rebellion to one of calculated strategic leverage.
Staying single-hypervisor is no longer the “safe” default—it is an active risk decision that assumes a vendor’s roadmap will always align with your bottom line. Even if you never move a single production VM, the act of architecting for the possibility via the HCI Migration Advisor is the only way to protect your budget and maintain sovereignty over your stack in this new era.
Multi-Hypervisor TCO Comparison
| Cost Factor | VMware (VCF/VVF) | Nutanix AHV | Proxmox / KVM |
| Licensing | High (Per-Core Sub) | Moderate (Subscription) | Very Low (Support Only) |
| Mgmt Tools | High (Bundled) | High (Integrated) | Low (Community/3rd Party) |
| Hardware | Strict HCL | Moderate | Very Flexible |
| Exit Difficulty | High (Vendor Lock) | Moderate | Low (Open Standards) |
Additional Resources:
- Gartner: Strategic Planning for VMware Renewals
- Nutanix: AHV Performance Benchmarks
- FinOps Foundation: Asset Management Standards
Editorial Integrity & Security Protocol
This technical deep-dive adheres to the Rack2Cloud Deterministic Integrity Standard. All benchmarks and security audits are derived from zero-trust validation protocols within our isolated lab environments. No vendor influence.
Get the Playbooks Vendors Won’t Publish
Field-tested blueprints for migration, HCI, sovereign infrastructure, and AI architecture. Real failure-mode analysis. No marketing filler. Delivered weekly.
Select your infrastructure paths. Receive field-tested blueprints direct to your inbox.
- > Virtualization & Migration Physics
- > Cloud Strategy & Egress Math
- > Data Protection & RTO Reality
- > AI Infrastructure & GPU Fabric
Zero spam. Includes The Dispatch weekly drop.
Need Architectural Guidance?
Unbiased infrastructure audit for your migration, cloud strategy, or HCI transition.
>_ Request Triage Session