Ransomware‑Ready Backup Strategy for 2025: What Every Engineer Must Know
In 2020, the advice was “have good backups.” In 2025, that advice is dangerously incomplete.
Today, backup infrastructure is not the remediation; it is the primary target. Modern ransomware cartels know that if they encrypt your production data, you will restore. But if they delete your backups first, you will pay.
Attackers now spend weeks inside networks reconnoitering backup consoles, stealing credentials for storage arrays, and identifying retention policies. If your backup strategy relies on a Windows backup server joined to the domain, dumping data onto a standard SMB share, your insurance policy is worthless.
For infrastructure engineers, the mandate for 2025 is clear: We must move from “backup retention” to “backup resilience.” This requires a fundamental re-architecture based on three non-negotiable pillars: True Immutability, Logical Air-Gaps, and Chain-Free Architecture.
Here is an engineering deep dive into building a ransomware-ready defense.

Pillar 1: True Immutability (Not Just a Checkbox)
Immutability is the state where data, once written, cannot be modified or deleted for a specified retention period—not even by a Domain Admin, not even by root, and not even by the CEO.
Many organizations believe they have immutability because their backup software has a checkbox for it. However, there is a massive difference between “soft” immutability (application-level software locks) and “hard” immutability (storage-level locking).
The Engineering Reality Check
If an attacker compromises the OS of your backup server, they can often bypass software-level locks by formatting the underlying disk or manipulating the system clock to expire retention periods prematurely.
The 2025 Standard: Storage-Level Locking
A ransomware-ready strategy requires immutability that exists outside the backup application’s blast radius.
- Hardened Linux Repositories (On-Prem): This involves deploying a Linux backup repository where SSH is disabled after initial config, the root password is discarded (or secured in a physical vault), and immutability is enforced at the file system level (like XFS with the
chattr +iflag activated by the backup software). Even if an attacker gains credentials to the backup console, they cannot send a delete command to the underlying storage. - Object Lock (Cloud/S3): The gold standard for offsite copies. Using S3 Object Lock in “Compliance Mode” ensures that no one—not even the AWS root account holder—can delete that version of the object before the retention date passes.
Internal Resource: Different vendors tackle this differently. For a comparison of approaches, see our deep dive on How Veeam, Rubrik, and Cohesity Architect Immutable Backups.
Pillar 2: The Modern “Logical” Air-Gap
The traditional definition of an air-gap (tapes on a truck) is too slow for modern recovery capability (RTO) requirements. In 2025, we rely on Logical Air-Gaps.
A logical air-gap is network and identity isolation that ensures the backup environment can survive total devastation of the production environment. If your Active Directory is nuked, your backup console must still be accessible.
The Architecture of Isolation
Your backup infrastructure should live in an “Isolated Recovery Environment” (IRE).
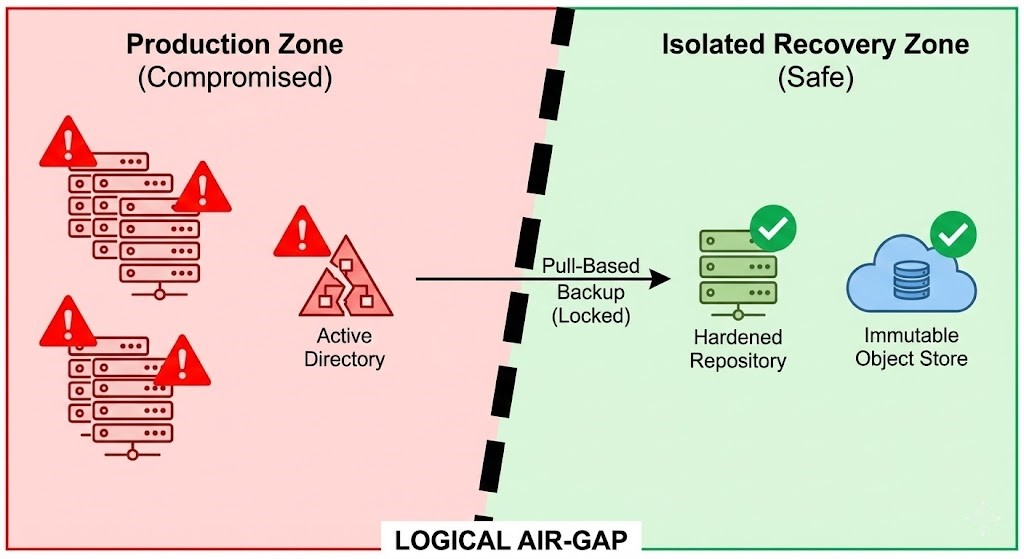
- Identity Isolation: The backup management console must never be joined to the production Active Directory domain. It should use local authentication or a separate, dedicated identity provider protected by rigorous MFA.
- Network Isolation & “Pull” Mode: Production systems should not be able to reach into the backup storage. Instead, the backup system should reach out and “pull” data from production over strictly firewall-controlled ports that only open during backup windows.
- Management Isolation: Access to the IRE should only be possible via a specific, hardened jump box or secure bastion host, never directly from a standard IT admin workstation.
If an attacker gets Domain Admin in production, they should look at the network and see a black hole where your backups are supposed to be.
Pillar 3: Chain-Free & Object-Based Architecture
The final pillar addresses recovery speed and reliability. Traditional backup architectures that rely on “forward incremental chains” (Full backup + Incr + Incr + Incr) are fragile.
The Problem with Chains
If ransomware corrupts a single incremental file in the middle of a 60-day chain, every subsequent recovery point is useless. Furthermore, restoring from day 59 requires the backup server to perform a massive I/O operation to “rehydrate” the full backup plus 59 incrementals before it can start streaming data back to production. This destroys RTO during a crisis.
The 2025 Standard: Object-First
Modern backup architectures are moving away from block-based filesystems and toward object storage (both on-prem and in the cloud) as the primary target.
Object storage, combined with modern backup software, allows for “chain-free” or perpetual-incremental backups. Every backup taken looks and acts like a full backup for restoration purposes, without the storage penalty of taking daily fulls.
- Resilience: Objects are inherently distributed and checked for integrity.
- Speed: Restores stream directly from the object store without needing a temporary “staging” area to reassemble chains.
The Engineer’s Checklist for 2025
If you cannot answer “Yes” to these five questions, your organization is vulnerable.
- Is our primary backup storage immutable at the filesystem/storage level (not just the application level)?
- Is the backup management console not joined to the production AD domain?
- Is MFA enforced on every access attempt to the backup infrastructure?
- Do we have an offsite, immutable copy (e.g., S3 Object Lock with Compliance Mode)?
- Have we tested a full-scale recovery assuming Active Directory and DNS are down?
Internal Resource: Moving long-term retention to cloud object storage is vital for resilience, but beware the costs. Read our guide on Cloud Cost Basics and Avoiding Sticker Shock.
Conclusion
In 2025, the measure of a backup strategy is not how easily it runs at 2 AM on a Tuesday. It’s how completely it can restore on the worst Saturday morning of your career. By implementing true immutability, logical air-gapping, and chain-free architectures, you move your backups from a target to an indestructible vault.
Additional Resources:
This architectural deep-dive contains affiliate links to hardware and software tools validated in our lab. If you make a purchase through these links, we may earn a commission at no additional cost to you. This support allows us to maintain our independent testing environment and continue producing ad-free strategic research. See our Full Policy.